- Stopping hackers:
- PCs
- Mobiles
- Apps
- On the street
- Circumventing censorship
- Psyops
Stopping hackers:
- Data security comes in two halves: security – stopping hackers getting your data, plus privacy – stopping hackers linking your data to you.
The UK state
- The UK is the biggest data spy in the world. Numerous government agencies can help themselves to your metadata without a warrant. Some government departments buy your data. Police hack mobiles and hide IMSI catchers to ID protectors or worse even in parliament.
- The UK spends as at 2021 £3.1bn on the intelligence organs MI6, MI5 and GCHQ, up to a third of which is outsourced. This is partly to launch a new Counter Terror Operations Centre for intelligence, police and justice co-location.
- Government, including police, spies, military, and even the DHSC, will be able to authorise your assassination under the Covert Human Intelligence Sources (Criminal Conduct) Act 2021 for being a dissident, by the ruse of certifying that you need an uncover investigation for national security, crime detection or disorder prevention or economic wellbeing and then arranging for the spy to need to kill you to prove their credentials to alleged criminals. They can then block a coroner’s inquest under the Coroner’s Act 1988 s17a by calling a public inquiry with terms of reference banning finding the truth and seal your records for 70 years, as was done with Dr David Kelly, whose death certificate was never signed by a doctor nor was place of death given on it. Protect your privacy like your life depends – it might very well do one day.
- Interception is hardly secret, as even before Snowdon’s stash (up to STRAP 2) was published with redactions of sources, the surveillance commissioner, parliament (see also ISC privacy & security report 2015) and ETSI published the gist of it, and telecoms industry knows what they can do themselves – which is simply what government can do more of with more money and influence.
- Surveillance is not only of communications but also facts such as your face or photos. You could argue that states surveil data not people, and only care about people once data triggers an alarm. However states might therefore only look where they expect or want there to be targets, and may have to invent targets to justify bulk data collection. See Hu’s Snowden taxonomy.
- It is curious that 9/11 came a few days after the EU published a report condemning Echelon, and that 7/7 came the month after launching SMAC (Sensitive Metadata Analytic Collaboration) Five Eyes metadata sharing was agreed in the Cheltenham Resolution.
- You cannot understand the threat from non-state actors without understanding the threat from state actors, and if government turns against the people you need to know your enemy, hence the below walk through of the UK Intelligence Community (‘UKIC’).
- Remember that the state has the Government Agency Intelligence Network (‘GAIN’), run on Alliantist Pam, which includes about 70 organisations such as transport and utilities being asked to make life difficult for targeted citizens.
JIC
- Joint Intelligence Committee (‘JIC’) is the pre WWII defence planning agency. They are responsible for analysis professionalism, tasking, international sharing, reviewing and alerting to threats, advising cabinet on collection and analysis priorities, and scrutinising agencies’ collections. Their mission is the same as the superset of UKIC missions: defence, foreign policy, economic wellbeing and serious crime. They consider assessments by the Joint Intelligence Organisation, whose job is assessment of reports and development of analysts.
- They led the UK into the Iraq War with the notorious ‘dodgy dossier’. The Butler Inquiry subsequently found them to be useless and the UKIC was resultingly Butlerised, with, for example, analysts forced to sit e-learning courses on how to word certainty to avoid sexing up reports.
- Until the Hutton Inquiry at least, the CIA head of London station sat on JIC for the first half of meetings.
- They use Tableau and PowerBI for analytics.
MI6
Mission
- MI6‘s mission is:
- obtaining information (HUMINT) about and performing tasks (eg kidnapping and torturing) against the actions and intentions of people outside British Islands to protect UK national security and economy and prevent serious crime,
- and has power to disclose information for any criminal proceedings but not to help a UK political party.
- If you do not engage in international conspiracies then James Bond is not coming for you, although on rare occasions he does help domestic operations, for example, if only they have expertise in an ‘effect’.
Collaboration
- The intelligence organs MI5, MI6 and GCHQ work simultaneously in separate fiefdoms yet also cooperate, with ‘integrees’ seconded to each other’s offices (and the NSA), and, for example, MI6 arranging renditions while MI5 attend the interrogations.
Staff
- Staff access to HQ on Albert Embankment next to Vauxhall Bridge is via tunnels, although there are a couple of pedestrian and vehicle entrances at street level, opened at peak times.
- Staff are crown servants.
- Recruitment has been handled by the agency GlobalSuccessor.
- Openly gay staff have been allowed in roles as high as chief of station since at least 1997, eg Christopher Hurran.
- Staff communications have gone over systems such as Noreen, Hora and Truncheon, and the old Automated Telegram Handling System from 1995. Abroad they have used Arramis via Scout terminals, Houseman phones or Cryptek fax.
- Retirees often continue to work a consultants through thinly veiled shell companies, some of which have been exposed online by amateur sleuths.
- Ex spooks include Charles Farr and PJ Riley.
- Security guards wear bullet resistant vests.

Sites
- The Vauxhall HQ benefits from a standoff plinth of reclaimed land to thwart small boats.
- Technical services department is at Hanslope Park.
- Training is at Fort Monkton.
Effects
- MI6 have some newspaper editors on the payroll, and others place fake stories to help out, such as the Telegraph and Spectator have done.
- Insiders have alleged that MI6 plotted to assassinate Milosevic and Gadaffi.
- There are four tactics to gather intelligence: spy yourself, recruit a spy, ask another country’s spies and hack.
- MI6 mainly provides single source intelligence without assessment.
MI5
Mission
- MI5‘s mission is to:
- protect national security from espionage, terrorism, sabotage, foreign agents or overthrowing of parliamentary democracy by political, industrial or violent means,
- safeguard the economy from people outside British islands, and
- help law enforcement prevent and detect serious crime (now transferred to NCA),
- and has power to disclose information for any criminal proceedings, but not to help a UK political party.
- This means MI5 could realistically be of concern to UK citizens at home, as it can theoretically help prosecute even minor crimes, and certainly spies on the population passively and then actively if thought a troublemaker for government or big business or thought a criminal by police or the taxman.
- Like GCHQ, MI5 meddled in Covid, seconding staff to the NHS to advise on bioweapon defence.
- The ‘national security’ part of MI5’s mission means the safety and wellbeing of the state. The ‘overthrowing’ part of their mission comes from the 1975 Lord Harris definition of subversion, which is wide enough to mop up dissidents who merely undermine rather than overthrow parliamentary democracy if that risks national security. They may say any attempt to interfere with parliament of government threatens national security as without it there is nobody to collect tax for and run the armed forces or vote to fund them. It would include MPs voting, or an anarchist party campaigning, to abolish parliament, even if the new system was to keep elections for governments, although it is thought not the abolition of the house of lords as long as the system of government remained. It should not include dissolving parliament or choosing a government as that is done by the queen not parliament. Before that, the Denning report in 1963 on the Profumo affair defined subversion as unlawful overthrow of government. Their previous crown prerogative charter was the 1952 Fyfe Directive: defending the realm against espionage, sabotage and subversion.
- About 90% of budget goes on counter terrorism, including counter proliferation, ISIL, IRA, right wing, left wing, anarchist and single issue, the rest going on counter espionage and protective security.
- Stopping jihadis means sabotaging flows of recruitment, money and travel.
- Generally stopping terrorists means sabotaging bombings, shootings, kidnappings and infiltration.
- Stopping spies means advising organisations on hardening, and tipping off about known spies or kicking them out.
- Stopping proliferation means making it harder to obtain equipment and know-how, eg by blocking exports and education.
Targeting
- Targets are ranked essential (not always covered), desirable and other.
- Ways to put yourself on their terror database, at least to be eliminated from enquiries, are to be suspected of killing, kidnapping, hijacking, aggravated trespass, stabbing, bombing or poisoning, or mucking about with WMDs, pathogens, nuclear sites or airports.
- There is a video about MI5 targeting muslem terror suspects.
- There is a video about anthropology of UK spying.
Collections
- Intelligence gathering is done by handlers running agents, and watchers, bugging, hacking, intercepts.
Elint
- MI5 handle domestic strategic and tactical national security metadata and content collection alongside NCA and HMRC who deal with serious crime and economic wellbeing.
- MI5 collections were upgraded under the Digint programme with the help of GCHQ and MI6.
- They run the IE domain database, which is similar to i2 and Palentir Government.
- They also run the Preston database of UK metadata from warranted phones and internet, but were found to only view 3% of what they collect and virtually none of it ended up in reports.
- They also get Milkwhite Enrichment Service metadata for IP targeting from GCHQ, as do NCA, PSNI, Met, HMRC and Scottish Recording Centre.
- Bugs are under warrant, as is the hacking or burglary to install them.
- Bugs are listened to live in multistreams per analyst for key phrases, before being archived for analysts to potentially listen to more fully later.
- Until the end of the 20th century officers had to crocodile-clip your street box if they wanted to intercept calls and modems. That is literally how one DG started their career.
Humint
- Case officers or agent handlers run agents who either approach MI5 for their own reasons or are targeted by MI5 as likely to be in a good position to gather intelligence. Such tipoffs often come from GCHQ.
- Watchers have to follow targets abroad sometimes. Some work is overseas anyway, on false identities. Covert staff abroad use unattributable Tryst mobiles.
- There is a leaked 1974 car surveillance instruction video, explaining the pickup, follow and housing.
Analysis
- They used IBM’s Attila for automated speech translation against PIRA, and trialled SAIL speech recognition. Transcription costs over £1,500 an hour and software is better at keyword alerting than transcription.
- Feeds such as Preston were viewed in Artemis.
- MI5 host the Joint Terrorism Assessment Centre (‘JTAC’) with staff from the agencies, DI, FCO, Home Office and police, which issues threat levels and reports on terrorist capabilities and intentions.
- MI5 mainly provide assessed intelligence plus some single source intelligence.
Staff
- MI5 claim to have 4,400 staff, in roles such as policy, cyber defence, software engineering, warrantry, legal, analysis, data, watchers, agent handling, information architecture, project management, HR, security and finance.
- Staff are crown servants, ostensibly employed by the MoD, despite the DG reporting to the Home Secretary, so are something akin to soldiers. For example, PTSD treatment is handled by the army combat street team.
- Ex spooks include Nick Trim and Steve Huxter who have effectively outed themselves through their cyber CVs.
- Recruitment has been handled by the agency TMP.
- Agents have died on duty, such as spy plane pilot Steven Lanham in 1999 and a surveillance officer who was assassinated by ISIS by ramming him off his motorbike in London.
- Several disgruntled ‘ex spooks’ have tried to forge media careers. ‘Marcus’ gives interviews, interviews and more interviews, and writes books, although insiders know his service was a long time ago if ever, given his stories like driving instruction which changed from what he was taught decades ago. ‘Robert Acott’ is another who went public after a mental breakdown. MI5 have let ITN interview disguised staff.
- “You can happily question our methods, we do that all the time. But don’t question our motives” – Spooks SE03EP06.
Sites
- MI5 regionalised in 2005, reflecting regionalised police Counter Terrorism Units.
- The only avowed sites are Thames House and Loughside in Palace Barracks, Hollywood, Belfast, but they also have hubs including Northern Operations Centre at Bury in Manchester, and technical support units, plus West London data centre at Feltham. The latter used to be confidential until MoD leaked it repeatedly, but has been known by bloggers and journalists for years (a spy thriller author even set a chapter in the building) and thus any foreign intelligence service worth its salt, in fact you can book an MoT or buy a used MoD car from there in theory; its only signs now are its building name and a notice to visitors that it is not its neighbour – although the window bars, green tinted glass, keypad (same models as Bury) and turnstile ought to be a clue you are at the wrong place.
- Thames House is the classic example of how you cannot always have the security you want. Whilst it benefits from the government secure zone of cctv and armed police, out front it has to make do with about fifteen feet vehicle standoff or twenty if a terrorist respects the cycle zone, round the back it is even worse with a normal pavement and building opposite and the side is worse still with a virtually non existent pavement and ankle height windows. PIRA blew up Thorney St in 1973 when the Home Office occupied Horseferry House opposite round the back, which is now Burberry.






- A video of Curzon St shows MI5 used to have less than ideal protection from IRA bombs, with a nice big concrete canopy over the pavement to maximise reflections to shatter the ground floor wall, a bomb refuge in the middle of the building and electrically operated bomb blinds that took several seconds to deploy.
- They also have Joint Support Units with law enforcement such as Roch Bank Place in Bury.

- Some staff are integrees in sister organs like MI6 or Five Eyes partners like NSA, and Europe has had a security service forum with a spook from each nation sitting together.
Collaboration
- They work with MI6, GCHQ, Border Force, NCA, PSNI, CTP police and government departments. Emails have for years been sent to sister organisations via Cluster.
- The DG runs JTAC and NPSA using staff from various government departments.
- It is said MI5 are better at combatting serious crime as they are higher vetted and stay in the job longer than specialist police, eg SO15 get kicked out after five years.
DI
- Defence Intelligence is part of the MoD’s Northwood-based Strategic Command, which has an organigramme.
- It collects intelligence to inform policy, crises, military operations and the agencies, and mainly provides assessed all source intelligence.
- It has some 4,500 staff, one third civilian reflecting a third of its work is for UKIC and other government departments (‘OGDs’).
- As at 2020 its:
- deputy chief of defence intelligence has civilian analysis and assessment directorates for:
- strategic,
- proliferation and
- capability:
- environmental/domains
- maritime
- land
- air & space
- cyber
- missiles, science & technology
- special projects), and its
- environmental/domains
- director cyber intelligence & information integration has a military directorate running commands for:
- counter intelligence,
- cyber & electromagnetic (Joint Cyber & Electromagnetic Group (‘JCG’) at RAF Digby), and
- Joint Forces Intelligence Group (‘JFIG’) at RAF Whyton, handling:
- humint (Defence HUMINT Organisation (‘DHO’), 350 staff, HQ at RAF Whyton),
- geographic (Defence Intelligence Fusion Centre (‘DIFC’) at RAF Whyton, 400 staff plus embeds from GCHQ and the US DIA),
- signals (Joint Service Signals Organisation (‘JSSO’) co-located with GCHQ & NSA at RAF Digby, with 1600 staff),
- imagery and geospatial (National Centre for Geospatial Intelligence (‘NCGI’), 500 staff, at RAF Whyton),
- Joint Aeronautical & Geospatial Organisation (‘JAGO’, 430 staff, £24M budget as at 2013, comprised of 42 Engineers Regiment (Geo) and Aeronautical Information & Documentation Unit (‘AIDU’)), and
- Joint Intelligence Training Group (‘JITG’) co-located with the Intelligence Corp at Chicksands.
- deputy chief of defence intelligence has civilian analysis and assessment directorates for:
NCA
Mission
- NCA is the UK’s national serious crime police force, specialising in:
- spying,
- helping forces with murder, kidnap and rape cases or advising on forensics, search, vulnerable witness, family liaison, profiling,
- spotting serial rapists and murderers using Violent Crime Linkage Analysis System (‘ViCLAS’) in Serious Crime Analysis Section (‘SCAS’), where about half of referrals are not looked at,
- combatting counterfeit currency, trafficking, money laundering, fraud, bribery, CSE, hacking, guns and drugs,
- running the UK Protected Persons Service (changing name and location, but not records),
- running the missing persons bureau,
- helping HMRC and Border Force,
- supporting Regional Organised Crime Units (some are co-located),
- and running the UK’s international crime bureau.
- Broadly speaking NCA gather intelligence on organised crime antics, combat them and supply specialist capabilities to other forces.
- NCA is organised into commands and teams in a matrix, with the vast majority in intelligence or investigations, but roughly speaking the structure is:
- Legal team of 40
- HR team of 45
- Capabilities
- National Economic Crime Centre (‘NECC’) formed by law enforcement (City of London Police, NCA, SFO, HMRC, CPS), Home Office, FCA and private sector, with a budget of at least £6M, 278 staff, thought to be now in three figures, delivering a weekly dashboard for partners:
- Teams:
- Threat leadership (452 staff, 23% powered, work with partners on 4Ps of pursue, prevent, protect, prepare)
- Asset Denial (unexplained wealth orders)
- International
- Money laundering
- Drug Money Laundering Intelligence Taskforce
- Proactive Money Laundering Taskforce (‘PMLTF’) with CoLP
- Bribery & corruption, largely funded by Official Development Assistance:
- International Corruption Unit, with 37 staff from merged proceeds and international corruption units
- International Corruption Intelligence Cell, joint with DiFID
- International Anti-Corruption Coordination Centre (‘IACCC’), funded by FCO
- Foreign Bribery & Corruption Clearing House
- Bribery Corruptions & Sanctions Group
- International Corruption Unit, with 37 staff from merged proceeds and international corruption units
- Fraud & market abuse
- Fraud Team – mostly investment fraud, produced Fraud Grid
- NCA CoLP Economic Crime Partnership Team
- Public Private Partnership (‘PPP’)
- Operational Planning Coordination & Delivery (‘OPCD’)
- Threat leadership (452 staff, 23% powered, work with partners on 4Ps of pursue, prevent, protect, prepare)
- Deputy directors for:
- UK Financial Intelligence Unit (‘UKFIU’), receiving around 600,000 Suspicious Activity Reports (‘SARs’) a year, loaded onto MoneyWeb industry database
- DFT (defence) & DML (terror) teams
- SARs Enquiry & Act Team (‘SEA’)
- Joint Money Laundering Intelligence Taskforce (‘JMLIT’) – 40 institutions
- UK Financial Intelligence Unit (‘UKFIU’), receiving around 600,000 Suspicious Activity Reports (‘SARs’) a year, loaded onto MoneyWeb industry database
- Teams:
- Operations, with 20 sites and £331M budget:
- Intelligence Directorate (supporting threat leadership, 2,302 staff, 637 powered), with five deputy directors for:
- National Intelligence Hub (‘NIH’)
- National Assessment Centre producing 70 assessments a year, including predicting new threats
- Economic Crime Desk
- Collections (forensic, Osint, CHIS, undercover and technical)
- International (taskforces, training, intervention, intel sharing, International Liaison Officer Network)
- National Data Exploitation Capability (‘NDEC’) launched in 2019 with a £30M budget to share data from across government on a self service portal after analysing it with artificial intelligence)
- National Tasking & Coordination (‘NTAC’, control centre and Regional Organised Crime Coordinators)
- With teams for:
- National Targeting Centre (working with Collection and International)
- Gateway (intel in and tasking)
- International Crime Bureau
- Sensitive Intelligence Unit
- Child Sexual Exploitation Referrals Unit
- UK National Office for the Suppression of Counterfeit Currency & Protected Coins
- Agency Facilitation
- Intelligence Capability HQ (‘ICHQ’, management for the directorate)
- National Intelligence Hub (‘NIH’)
- Investigations Command (disruption, 1,952 staff, 1,283 powered, eg social workers, surveillance, financial; top 25 cases updated on weekly Grid, uses Atlas case management software, 1,200 caseload, most SIOs lacks PIP3, automatic secret classification on Atlas means investigators can’t get online or share info easily on non secret info, worse surveillance kit than SOCUs)
- Three deputy directors covering north, south and midlands, Wales & west.
- Teams:
- Illicit Finance Surveillance Team
- SCAS
- Major Crime Investigative Support Unit (‘MCIS’)
- Special Research Team
- Witness Intermediary Team
- National Injuries Database
- Crime Team
- Expert Advisers Database
- Crime advisers & Digital media specialists (device inspection outsourced)
- National SIO Advisers (‘NSIOAs’) for north, south west & south east, eg DCI Noel McHugh
- Crime investigation support officers (seconded DSs)
- National Search Adviser
- National Interview Adviser
- National Family Liaison Adviser (eg killer stepdads)
- Behavioural Investigative Advisers
- Geographic Profiler
- National Forensic Science Adviser
- National Missing Persons Adviser
- CATCHEM child murder database
- Forensic Clinical Psychologist
- National Vulnerable Witness Adviser
- Expert Evidence Team
- Expert Laundering Evidence (‘ELE’) Cadre (reps from 13 agencies)
- Missing Person Unit
- Missing Persons Bureau
- Missing Childrens Team
- Vulnerable Persons Team
- Anti Kidnap & Extortion Unit
- Special Operations Unit, covert surveillance against drugs guns money laundering & CSE, uses surveillance dashboard, Chronicle & APMIS (agency partners management information system, linking to forces and ROCUs)
- Armed Operations Unit
- Organised Crime Partnership (drugs & guns, with MPS)
- Anti kidnap & extortion unit
- Dedicated unarmed surveillance team
- Threat to life cadre
- Intelligence Directorate (supporting threat leadership, 2,302 staff, 637 powered), with five deputy directors for:
- Threat Leadership, with deputy directors for:
- National Cyber Crime Unit: Head of Technology Paul Edmunds, officer Zulfikar Moledina.
- Crypto Cell launched Jan 2023, 5 officers
- PROTECT: Mitigtation at Scale (compromised passwords)
- Borders, Organised immigration crime, Modern slavery, human trafficking & Commodities
- Modern Slavery & Human Trafficking Unit (‘MSHTU’)
- Child sexual abuse & exploitation & UK Protected Persons Service
- National Cyber Crime Unit: Head of Technology Paul Edmunds, officer Zulfikar Moledina.
- Police counter terrorism is led by the Met’s SO15 who work as enforcers and tippers for MI5, and with Border Force, Interpol and UKIC. They have their own surveillance engineers at Cobalt Square, etc.
- NCA is organised into commands and teams in a matrix, with the vast majority in intelligence or investigations, but roughly speaking the structure is:
- The NCA DG can order chief constables to put forces at their disposal and the Home Secretary can order the NCA to help forces. But PSNI chief constable has to approve covert techniques in Northern Ireland. And NCA cannot order ROCUs to help.
Programmes
- Despite what was Special Branch sitting in CTP (with some 1,500 staff), NCA use National Data Exploitation Capability (NDEC) in Operations Intelligence Command (with about 2,000 staff managed by a director and six deputy directors for Collection, National Intelligence Hub, International, Tracer, National Tasking and Co-ordination, and NDEC) to analyse government data for national security, using systems built with Python on AWS assisted by AI, at Citadel Place in London and the south west of England. They have been using Jupiter, Kabana, SQL, GitLab, Elk stack and Terraform.
Staff
- They have around 5,000 staff in total, increasing to 6,000 as at 2021, of which 1,250 are investigators. About 140 staff are overseas at about 68 offices in 49 countries. The Nawasi Brigade stormed their Tripoli makeshift base in 2017.
- NCA officers can be tripled warranted as constables, immigration officers and customs officers. 64% of officers are ‘non powered’ so not ‘operational’, some are purely researchers. Most staff are at grade 4 or 5 so equivalent to police serjeants or inspectors.
- NCA officers have for years had no panic buttons so would have to ring 999 for backup. Some do not have Airwave.
- NCA often siphon off ROCUS officers or even whole teams as the vacancy rate is enormous.
- ROCU Regional Organised Crime Coordinators should be indoctrinated in classified capabilities of the UKIC which are accessed via NCA.
- ROCU spokesmen are publicly listed, but could play havoc with your phone if you rang them, so best not.
- ROCUs rely on fixed term funding so struggle to keep good staff.
- ROCUs struggle to share classified information as everyone has different IT, including the SFO.
- ROCUs are hard to task due to bureaucracy so usually forces keep the biggest gangs to themselves and palm off smaller fry for ROCUs to chase. Even when a gang is escalated from the force to ROCU, the lead responsible officer in the force may plough their own furrow while the senior investigating officer at ROCU does something else.
- ROCUs are supposed to lead investigations but instead tend to be tasked with supporting forces.
- ROCUs are accessed by forced through a single point of contact with a gateway team including a GAIN coordinator assessing potential taskings.
- ROCUs are routinely used as a cyber and fraud squad by forces.
- Some ROCUs work alongside regional Counter Terrorism Units, eg ERSOU houses ROCU and CTP for east of England. ERSOU has 130 staff in its Cyber & Economic Directorate.
- ROCUs include a Regional Economic Crime Unit who confiscate assets for NCA and forces.
- NCA officers all all SC Enhanced cleared, and some have to upgrade to DV Enhanced.
- NCA also have volunteer specials.
- Staff have a trade union, the NCOA.
- At DG command level candidates are interviewed by a panel including a civil service commissioner, chief constable and the GCHQ director.
Sites
- HQ moving to Stratford in 2025
- NCA Joint Operations Team in the north west of England (secretbases says Olympic House, Longbarn Boulevard, Birchwood, Warrington) works with the UKIC, eg GCHQ on CSE.
- NCA Regional Operations are embedded along with with HMRC and Border Force and ROCUs, eg NERSOU at Sunderland, EMSOU at Kirkby, WMROCU at Defford.
- ROCUs tend to be based at motorway junctions.
- NCA sometimes refuse to work with ROCUs and instead focus on London leaving ROCUs to their region.
- Secretbases say NCA have a site at Gatwick, Stevenage and Ascot, plus a lab at Tamworth, Warrington and Abingdon, and suspected sites at Manchester, Portishead Down, and certainly a past site at Trafford Park Manchester.
Capabilities
- Their budget is about £0.5bn.
- NCA have used Mercedes Viano vans as nondies.
- To get an idea of potential police tactics, read Menu of Tactics to disrupt gangsters lifestyle, behaviour, vehicles, travel, business and crime.
- NCA take two guns off the streets a day, make three arrests a day and get one conviction a day on average (almost all plead guilty).

NCTIU
- The National Counter Terrorism Intelligence Unit is another threat to dissidents which spies on protestors against government policy.
- It is the renamed version of NDEDIU, itself the renamed NPOIU, itself the renamed discredited SDS, previously called NDET. The implication is that demonstrators are terrorists.
- Although they have traced one bomber, their main claim to fame is having babies with protestors by forming relationships under false identities such as Mark Kennedy, John Dines and Bob Lambert, smearing murder victims’ families, hiring Indian hackers to steal journalists emails (many officers refused to deny it) and trumping up charges against innocent protestors leading to collapsed trials.
- Having shredded documents to cover up crimes during the Undercover Policing Inquiry and IPOC’s Operation Gilbert, they appear to remain an organised crime gang.
- Their MO online is ‘Socint’, using open source social media to scan for keywords, networks and sentiment.
GCHQ





Summary
- GCHQ:
- mission is to:
- monitor, use and interfere with emissions and their equipment and to obtain information from it and encrypted material,
- advise and assist government, armed forces and the public on languages and cryptology and information security for protection of national security, protection of economy against actions or intentions of people outside British islands and prevention of serious crime,
- is a commissioning authority (about a third outsourced) that develops, buys and sells both technology and permission to intercept, and uses armed forces for some of its work,
- specialising in:
- permanent bulk intercept via masts and telecoms providers (whereas temporary targeted intercept is more BSS (MI5)’s job),
- filtering,
- analysis,
- hacking (to degrade – ‘computer network attack’ or ‘effects’, or spy – ‘computer network exploitation’ or ‘exploits’),
- cyber defence (‘computer network defence’) and
- psyops,
- split between many sites doing collection and exploitation with:
- collections mainly at:
- Bude (NSA transatlantic cables, shared with NSA’s Carboy and
- Cheltenham:
- privatised FM,
- 1.1M square feet,
- 600 feet wide,
- 70 feet high,
- quarter of a million tons of concrete,
- Albert Hall sized computer hall,
- over 100 IT systems,
- 5,000 miles of cable and 6,000 miles of wiring,
- goods train in basement,
- 13,000 square metres of glass, masked by reflective 1.5m x 4m sacrificial planar blast curtain wall which in a blast flaps like a sail and turns opaque,
- 11,000 square metres of aluminium roof,
- Cotswold limestone-faced concrete anti-blast walls at ground level with granite elsewhere,
- c. 4,500 staff, mostly living in Cheltenham, over 2,000 staff elsewhere plus hundreds of contractors, staff are civil servants, many staff are from time to time deployed to the front line, although civil servants staff hold GCHQ grades prefixed GC – usually GC10 which is an Executive Officer in the normal civil service, recruited with the help of TMP for verbal reasoning tests, ProveIT for IT tests and SHL Solutions for psychometrics, with interviews arranged via Saba.
- Scarborough, Manchester and London (Westminster) being the only other avowed offices, although Harrowgate (run by NSA as Moonpenny at Menwith Hill Station (‘MHS’), running drone strikes etc with satellites being demodulated to track phones etc) and Lincolnshire have been acknowledged,
- other sites with dishes such as Edgehills and Widecombe-in-the-Moor,
- NSA run EUCOM’s RAF Molesworth,
- international cable amplifier stations such as Pottington , Hunmanby, Brean Sands and Highbridge,
- outposts like RAF Digby (thought to have its Russian aviation work offloaded to Elmendorf,
- partnering through co-labs, HIMR (on data mining, quantum computing, algebra, probability, data science, number theory, combinatorics etc, see example paper on terrorism) via Information & Communications Technology Research (ICTR) business unit (the equivalent college for NSA in USA is CCS Bowie), and research fellowships, and NCSC partnering with the Engineering & Physical Sciences Research Council and Academic Centres of Excellence in Cyber Security Research (and possibly UKVAC charting flight data), and
- organised in departments like ICTR with teams like MCA and DMR (data mining?),
- phones have included Brent and Russett.
- collections mainly at:
- tasked with:
- using cyber to give the UK the edge against:
- gangsters (eg hackers, smugglers, paedo rings and money launderers, including 350,000 gangsters in the UK in nearly 5,000 gangs),
- terrorists (eg taking Daesh offline),
- spies and
- enemy forces (counter proliferation and weapons collection),
- but also extremism, proliferation and crisis response, or whatever the priorities in the National Security Strategy as updated by National Security Council and Joint Intelligence Committee, eg brexit, climate change and keeping sea lanes open.
- using cyber to give the UK the edge against:
- Outed by Duncan Campbell in 1976, when they were still calling themselves CSOS.
- mission is to:
Mission
- GCHQ operates in the cyber battlefield through its intelligence & effects directorate with:
- attacks (sometimes by fourth party collection, which is hacking the enemy’s hacked data, either passively at midpoint if unencrypted, or if encrypted then actively or directly (victim stealing) by going to the endpoint),
- exploits (implants beaconing availability and extracting exfiltrates), and
- defence (part of assurance at NCSC, strengthening antivirus software, working with industry, network monitoring, red teaming, defensive implants, IP blacklisting, redirecting DNS, quarantine traffic, neuter or insert malware, honey tokens, honeypots, honey nets, false flag, effects, implants for Opsec monitoring, pursuit to recover binaries, Quantum insertion, pursuit to implant on / disable / destroy adversary infrastructure, blocking hacks and identifying actors and reasons, finding botnets, smuggling or steganography through data mining, eg random forest algorithms – similarly you can listen to IED triggers for their signature).
- Their job is signals (emissions, equipment, languages and decryption) and assurance (eg encryption), to protect national security, the economy and against serious crime, although have unilaterally taken on health too.
- One might assume that GCHQ are like MI6 in that they spy for British big business in interpreting widely the ‘protecting the economy’ part of their mission. We know NSA do for USA firms. There would be more pressure on MI6 to help firms as they use firms overseas branches as sources with their own relationship managers.
- There is not much scope for spies to target random citizens as firstly collections are increasingly bulk and secondly exploitation is increasingly struggling to keep up with collections. Historically even warranted collections were mostly not read. Nobody is sitting in Cheltenham reading your emails and phone transcripts unless you are very exciting.
- GCHQ try to influence policy, law and treaties on signals and cyber.
- HMG clients include:
- Bank of England, who they update on credit, hacking and G10,
- Cabinet Office, who they help with national security policy making, technical support and crisis management (eg they are copied in if Cobra called),
- DCLG, who they advise for local authority cyber security and Prevent and loan Government Communications Officers,
- influencing energy policy on energy security and climate change by revealing foreign stances,
- DEFRA, who they help on carbon trading and CBRN planning,
- foreign aid, which they help with intel (eg corruption, security and elections) and cyber security,
- overseas investment, for which they advise on credit risk,
- FCO, who they help with policy and loan GCOs to Whitehall and in theatre,
- FCA, who they sell a dedicated analyst for financial crime looking at terrorism, boiler rooms, foreign infiltration, stability and fit and proper application intercepts, and advising on intercept as evidence,
- health, for which they provide cyber security and occasional GCOs, and
- transport, for which they advise on cyber security and terror intel.
- GCHQ mainly provides single source intelligence without assessment.
Regulation
- Investigations have to be justified by source, purpose, priority and human rights justification under ISA94 (hacking), HRA98 (proportionality), RIPA2000 (taps) and WTA06 (radio). WTA06 s48(3A) decrimimalises lawful intercept of wireless telegraphy under IPA16 Part 2. However, as we know GCHQ illegally collected bulk comms metadata and personal data until parliament found out in 2015, it would be naive to believe they stick to the law. Authorisation depends on technology, whether there is a warrant, what country is targeted and whether it is Five Eyes.
Programmes
- ??
NCSC
Cyber offence
- ??
Cyber defence
- GCHQ have run the Gordian Knot cyber defence programme.
- They monitor for hacks against the UK using Haruspex to seek signatures, reports on which are sent to clients via Prospero.
- PREVENT also feeds in to GCHQ, and contacts with schools are also used to set up CyberFirst classes to increase the pool of potential cyber warriors, but secretly also as a psyop to wrap around budding hackers identified by schools under the pretext of cyber safety classes. They also have relationships with colleges for outsourcing odd specialists jobs and tipoffs about potential recruits.
Covert infrastructure
- GCHQ hack strangers’ computers to turn them into operational relay boxes to be used for as covert infrastructure eg for DDoS, exploits and exfil, under programmes called Hacienda (wordwide port scanning by country according to Geofusion IP lists, built by JTRIG CITD with ports and protocols from subscription to Censys, lookup in GlobalSurge, used for CNE ORB detection and vulnerability analysis and signals development network analysis and target discovery), Mugshot (device characteristic logging for target and non target machines), Combine Harvester and Highnote. You would need to explore defences such as port knocking to avoid being used like this, although Five Eyes countries are not used by Five Eyes hackers.
- It has to be assumed that, like NSA, GCHQ infiltrate staff into telecom and hardware firms and embassies for humint and interdiction, especially as decryption is described as ‘fragile’, ie perhaps staff could be rumbled or sacked at any moment, in addition to paying RSA $10M to use a waterered down encryption key.
- Another trick is deanonymising TOR users by comparing cumulative packet counts at guard and exit nodes, which appears to need them to own exit nodes to which they try to herd users; other possibilities include taking over rendezvous points and hidden service directories and matching cookies on and off TOR. GCHQ’s TOR bridge discovery prototype was called Homing Troll. Their hidden services host name database is Hidden Selection. They hoped Tribal Carnem IP session metadata would help deanonymise Tor.
- In the UK government can issue Preston warrants to tap a line; these produce about a million items a month.
- Special source collection secrecy is protected by a community of interest called Chordal.
- The biggest programme is Tempora.
- Developed from TINT offline research space and CPC internet buffer experiments that enabled hacking and end product reports.
- Deep dive special source exploitation strips out 70% of traffic such as P2P and tries to pump the best 7.5% of intercepts filtering by keyscores, technology and IP subnets into massive volume reduction. This helps find targets for interception or hacking.
- Part of what originally called Mastering The Internet Enhanced Discovery Special Source SIGNINT, shared with NSA.
- NSA’s XKS is one component of Tempora, as is Massive Volume Reduction, Special Source Exploitation Access and Pokerface sanitisation.
- Each of the at least 200 lines out of GCHQ processing centres Cheltenham (‘CPC’), Bude (‘RPC1’, tapping landing stations at Stockport, Yarmouth, Dover and Brighton) & Leckwith (‘OPC1’, or ‘Circuit’ at Seeb, Oman shared with the Sultan of Oman’s Air Force, with three sites, Timpani (covering Iraq), Guitar and Clarinet (covering Yemen – where GCHQ targeted alleged terrorists for assassination by drones), tapping nine international cables in the Straight of Hormuz) for taps is a ‘bearer’ attached to a probe at a bandwidth of at least 10gb/s, but not all can be on cover at once so cover is cycled by checking each bearer for relevance on the Flexible Knowledge Base. OPC2 location is unknown.
- The data hoovered up is subjected it to massive volume reduction using packet processing framework filter hardware feeding into Terrain software for sessionisation and then further narrowing down. Content is buffered for three days and metadata for 30 days.
- Metadata is pulled in unselected to be analysed on the Next Generation Events software (metadata being events such as a call) and to Oracle-based Query Focussed Datasets such as Five Alive (recording five fields per record (‘tuple’) for IP events at a million events a second into Distillery), running through Oracle on Redhat on 15 petabyte HP blades as at 2012, for traffic per IP or near real time stream processing in Distillery or the map reduced cloud, but content is filtered according to selectors on the Broadoak targeting database. This does not mean full take content is not kept and used. This data is processed where it is filtered so has to be queried remotely from Cheltenham, largely as the volumes are massive. A thousand machines were used to process 40 billion records a day as at 2011.
- Personal processing is done via Linux Interactive Desktop on Redhat. Alternatively, Linux compute clusters included the 5,216 core Mount McKinley.
- Tapping sites include in Hong Kong, Germany, Cyprus and Singapore.
- Tempora was hoovering up 10 billion records a day back in 2009 via buffers into bulk files stores like Technology Research team’s Black Hole flat file store 217TB in size, as part of Blazing Saddles within Next Generations Events programme, interrogated remotely via http interfaces Blackfind and Blackcat, and ending up in QFDs like Mutant Broth, Auto Assoc, Karma Police and Infinite Monkeys, access on desktops via Looking Glass plugins. One database was already 1 petabyte in size and taking 32 billion events in 2010 and a database of web visits was taking 50 billion events a day in 2012 so probably up to about 15 petabytes and 750 billion events a day by 2021.
- Tempora uses Xkeyscores (filters with selection, 75 servers, 8,000 users) like Tempora deep dive special source access programmes to hack trans ocean fibre optics and store a buffer of 3 days’ worth of about 30% of internet traffic on 1,000 machines hoovering up 40 billion items a day (in 2009, probably at least 100 billion based on world internet users as at 2020) for analysis using Genesis programming language ‘fingerprints’. They probably had over 10 terrabits per second coming in a few years ago and can sample at least 25% of internet traffic coming in and out the UK over 1,600 bearers and process probably several terrabits per second. Cables are intercepted at access points, backhauled to processing centres and accessed by analysts at yet further sites.
- Other special source projects have included Muscular (Google & Yahoo) and Incensor. Incensor, Quantum, Turbine and Turmoil automated man in the middle and side attacks are run from Menwith Hill. Incensor is Vodafone tapping another firm’s cable at Skewjack Farm (Nigella) and onwards to Bude.
- Paul Deitrich has knocked up a GCHQ cable ‘radioactivity chart‘ based on how badly penetrated cables are by GCHQ, although it dates back to 2010 and Five Eyes and new partners are also a threat.
- Several cable stations are disguised as bungalows but are given away by ventilation louvres as pointed out on Cryptome.
- Phone data goes to the legacy telephony events database Salamanca, and to Sunstorm and Distillery databases, at about 5,000 events a second, some in-country but mostly international. Once collected it is ready to be exploited through database queries and reports.
- Near real time presence alerting comes via Samuel Pepys event diarisation database from Terrain event generation, covering page requests, logins, searches and phone location.
- Muscular is the programme intercepting traffic at social media providers.
- Hidden Otter was the Hadoop Remit Chains algorithm for finding hidden temporal chains such as TOR, backhaul or botnets. It was not made easy by each source and probe having its own clock unsynchronised.
- Salty Otter was a CLASP-based cross media hunter which finds linked communications such as calls asking someone to IM them.
- Bakers Dozen was an algorithm to find causally, eg temporally, connected sequential phone numbers, eg to catch a terror cell using a job lot of burner phones to ring the same third party. These sorts of algorithms use Poisson processes. The time link might not be proximity but homogenous distance, eg GCHQ staff do not call their personal mobile mailboxes during shifts, so if you had access to Cheltenham metadata you could find numbers of suspected spooks by looking for phones logged to the nearby masts and filter for long gaps between calls and then ID them from those selectors. This is already presumably done with jogging apps. Similar algorithms are used against Twitter hashtags. Other algorithms can spot other patterns, such as a terror cell or other ‘closed loop’ all replacing their SIMs at once and thus standing out like a sore thumb as an outlier event. Closed loops can be confirmed by the handsets being cheap (like the 7/7 bombers’ Nokia 1100s), and the nodes starting at the same time, being abandoned within a few months and most being used within a few weeks. They are found by ‘windowing’ – looking for groups using burner phones amongst themselves over a few days during which they will probably not accidentally phone an outsider and thus not come up on the closed loop search. Closed loops became a subject of concern after the 7/7 bombers used one and as a result GCHQ analysed UK calls to find how common they were.
- GCHQ’s inhouse IM was called Pidgin.
- Crown Prince finds Apple UDIDs in HTTP traffic. Once handsets are matched to their synching PC the PC can be implanted to implant the handset.
- PRIME testing for government networks was outsourced to Roke, who still act as outsourcer or consultant on national security data.
- NCSC Tempest testing labs are outsourced to firms like TUV SUD.
- GCHQ has approved encrypted email for government such as Egress, albeit with only AES 256.
- A Five Eyes favourite piece of kit for cyber defence sensors (for EonBlue passive sigint deep packet inspection tracking by signature and discovery by anomoly from special sources and into an alerting engine) is the Dell Poweredge eg the R610.
- NCSC offer a voluntary cyber defence server to copy metadata to GCHQ ‘for your own safety’, Police CyberAlarm. This is as suspicious as Darktrace, an AI cyber defence server launched by spooks.
- GCHQ’s projects have included:
- Stargate graphical query engine for endpoint exploit manual authorisation and Daredevil remote forensics,
- Rock Opera remote indexing,
- Goldeneye content metadata store,
- Lookingglass endpoint enrichment,
- Carbon Rod MITM vulnerability assessment,
- Highnote CNE target development,
- Lunar Hornet implant visualisation,
- Jackpot implant callback log.
Techniques
Targeting
How
- Typically, targeting relies on a seizure, open source (‘OSINT’) or informer (‘HUMINT’) giving a seed selector (eg suspect’s phone number) and then contact chaining to out-neighbourhoods of who they ring and who in turn those people ring and so on, with the selectors normalised, expanded and queried. But in counter terror GCHQ may not know who to even start with, so instead they may have to use algorithms (eg Laumman) or look for clusters (eg on GCHQ’s Dynamic Graph like dynamic graphs) to find modus operandi such as payphones and burner phones. Other algorithms such as low rank approximations can be deployed to hunt spot MOs. You also have to assume GCHQ have their own version of NSA’s Cotraveller which extracts mobiles that log and and off the same masts on a journey to identify associates, and of tools to track which mobile has moved from abroad to the UK. COMSEC behaviours, such as mucking about with power button, SIMs or swapping phones, would trigger closer attention. Some targets are sacrificial, like innocent sys admins or staff at satellite manufacturers, who are hunted and loaded on a database as a back door into networks. Typical relationships are time, place, number and equipment. Chaining involves filtering and scoring.
- Targeting can involve looking at pattern of life, modus operandi and technology used.
- The countermeasure to targeting is to be invisible, failing which be normal, failing which do not use electronics, failing which do not have selectors, and avoid contacts.
Who
- Targets might be not only innocent but friendly, for example, identified via a false flag social media platform used to attract potential dissidents to campaign against an unfriendly regime, as NSA did in Cuba.
- They hack hackers (fourth party exfil) as the best hackers often target GCHQ targets, and one such database is Intolerant.
- You might expect targets to be countries, regions, counter cyber, providers and counter terror.
Databases
- Targetting is logged on the Broadoak database.
- They have a vulnerability database called HiddenSpotlight.
Selectors
- GCHQ argue that they need bulk intercept to store everything long enough to scan for targets’ metadata against strong selectors and again to perform complex searches without strong selectors.
- Websites of interest and target selectors are classified UKEO so not shared with NSA.
- GCHQ target IP addresses, domain names and new exploits by tracking mailing lists, Pastebin, chatrooms, Github, databases, twitter and blogs. These are stored in Happy Trigger, Zool and Two Face databases.
- They have an IP address wiki called PositivePony.
Contact chaining
- The 7/7 bombers were contact chained on a tool called MOAG (presumably Masters Of All Galaxies).
- Contact chaining visualisation has been done through a programme called Chartbreaker using i2 and Mamba tool fed by databases including Sorting Friends (NSA’s R62 joint telephony invention, clusters strongly related phone numbers), MoaG, Snapdragon (C2C), Primetime (telephony analysis timing) and Carpat (filter). Contact Lens queried Fleximart VLSP data.
Collection
- GCHQ collect signals intelligence, mainly communications, via masts, dishes and network access points, but sometimes specific intercepts between access points.
Decryption
- They ran the UK end of NSA’s decryption in Penetrating Target Defences team (opposite NSA’s CES), under Five Eyes community of interest Bullrun (and Picaresque, Pawleys & Ambulant), to attack SSH, SSL, HTTPS, Ipsec, VPN and encrypted chat and VoIP, sometimes only metadata, using not only cryptology but cryptovariable recovery to speed up decryption, secret modifications to cypto tech to circumvent encryption, and secret partnerships (ie providers allowing access and leaks and tech firms helping NSA decrypt) that leak vulnerabilities to allow it, with data stored on NSA’s Longhaul and decryption on Gallantwave programme HP servers, and collection via midpoint passive collector Turmoil & Turbulence programmes and Poisonnut & Scarletfever cipher recovery. In USA the NSA’s Longhaul programme behind decryption was partly built by contractors Sotera, McLendon, Digiflight and Softech Solutions. Longhaul is an attack orchestrator using pairing and crypt attacks.
- The two categories of decryption are cryptanalysis and side channel / implementation.
- Cryptanalysis methods include obtaining a plain text and its cypher for clues as to how to unmask another text. Another is to deduce one key from another in a public-private pair. Another is to find a pattern left over in the encrypted text from the plain text. Another is a birthday attack on hash functions, exploiting the birthday paradox that coincidences are likely, eg the probability of two of 23 people having the same birthday is 50%, to find multiple variable length messages hashing to the same fixed length digest, which only needs computations of 2 to the power of half the bit length. Differential cryptanalysis of block ciphers requires 247 chosen plain texts so it not hugely practical other than for smartcards or devices with no filtering, anti-tamper or timing randomisation, and looks for probabilities in each round of encryption to reveal key bits one by one. Linear cryptanalysis requires 247 known plain texts to find probabilities to exploit lack of randomness. Brute force decryption as at 1998 could break DES in 56 hours for USD 250,000 judging by an EFF experiment. As at 2012 Tor, Truecrypt and OTR, and on occasion at least PGP, were problems for NSA, but we have to assume by now GCHQ have either circumvented them or have enough IBM in their computer hall to at least decrypt one target at a time. NSA considered trying a Tau statistic attack on AES. The obvious ways to protect encryption are to use a long random non-repeating key and a short message.
- Implementation attacks exploit encryption hardware imperfections such as power analysis (measuring consumption during encryption, especially if lacking capacitors and smoothing software), timing analysis (of relationship between input and key if you know how the cryptographic module works, especially if it lacks timing smoothing or randomisation and blinding (multiplying ciphertexts by random numbers)), fault induction (microwave, heat or voltage to use errors to discover keys), acoustic (listening to chips process with a mobile phone next to them), electrical (measuring computer chassis potential via ethernet cable) or Tempest (snatching keystrokes screen displays or keys by emissions).
- Another method of decryption, of course, is brute force, such as spending hundreds of millions of pounds on a computer that can crack a 1,024 bit Diffie-Hellman prime number. Bear in mind that encrypted texts from 2000 under RSA 512 can be be decrypted at home for a few quid on Amazon EC2. Also Diffie-Hellman can be cracked by finding discrete singlr logs of public values. Another options is Logjam, a MITM TLS attack that lowers to export grade encryption where elliptic curve is not used. Using a supercomputer with ASIC, DHE 1,024 could be cracked in a year on £100M worth of kit, although it only needs to be done for some DH groups to unlock many VPNs.
- GCHQ use techniques including pairing, such as of plain text and cypher text samples. They are also consulting academic on quantum computing to speed up decryption. No cypher is ‘unconditionally secure’ except a one time pad, so given enough computers you can decrypt if you have enough cypher text as examples. Adversaries rely on GCHQ having to spend more on computing than the secret is worth or only cracking it when the secret has become stale.
- Decryption hardware is likely to be IBM WindsorGreen which can crack 1,024 bit RSA. NSA used to use IBM 3650 (M3s it appears), HP DL180 and Dell 2950 within their decrypt enclave. GCHQ probably used similar as they also used the same Cavium decrypt card and have been sys admins on NSA’s IBMs. Given that GCHQ hid a secret double budget for Zircon, you might think that when inexplicably they went over budget by £409M in 2004 for the move into the doughnut the cash actually went on a crypto supercomputer.
- One ruse deployed was selling encryption machines to developing countries which GCHQ had the key via Swiss front company Crypto AG.
- With physical access to the machine, several options become available to extract keys, such as cold booting. Defences include physical security, gluing DRAMs, powering down when not in use, disabling USB, avoiding precomputed encryption, memory scrubbing, key expansion and encrypting in disk controller.
- One partial countermeasure is to encrypt all your emails so that encrypted ones do not stand out as sensitive ones.
Strategic
Tactical
- Tempest security involves introducing conductivity gaps such as filters and non-ferrous shields for cables, special cases for equipment, non-conductive sections in utilities and building fabric linings such as copper and window film, such as Glasslock Spyguard and Datastop air traffic control glass, to stop UV (monitors), IR (laser microphones) and RF and microwave (phones, EMP, ELINT). Modem lights, screen reflections, metal fences, mobiles (as a carrier signal – NSA codename Nonstop) can all leak signals from computers. Cables can betray power variations allowing an attack codenamed Hijack. Another attack is to irradiate equipment with microwave to create harmonics or to pick up harmonics, eg from a keyboard cable.
Metadata
Content
Passive
- Twitter posts are scraped via RSS to GCDesk which is accessed via unstructured LovelyHorse wiki front end. Structured datasets go in HappyTrigger. Another front end is Palentir analytics platform with Swing-based GUI, which it appears replaced the inhouse desktop integrator Monte Vista. Of great interest to GCHQ are cyber security academics who may publish zero day exploits for example, although ISA are assumed to buy exploits from brokers who charge up to USD100-250k for new devastating vulnerabilities. LovelyHorse website is a TCP open source capability, run by CDO team, powered by Birdstrike Twitter feed, accessed via HappyTrigger, GCDesk and RSS feeds, with targets suggested by Dettica, used for example to learn hacking techniques from hackers and to avoid analysts having to waste time wading through blogs via Jedi terminals or at home.
Active
- NSA use tools like Google PittPatt for facial recognition of emailed passport photos into Wellspring, and they collect border biometrics into Pisces and photos and use satellites imagery to locate photos.
- The three ways to collect are monitor, acquire and defeat, in other words, look up, steal and break, and the two modes of collection are active – bugging (MI5’s speciality), and passive – bulk tapping (GCHQ’s speciality), and the two intentions of collection are targeted (eg querying a database for a suspect) and untargeted – because you are still looking for targets (eg bulk data), and the two points at which you collect are terminal – at your target person or data (eg a terrorist or bulk call records), and enabling – at a gateway en route to your target (eg a sys admin or encryption key).
- The threat from the state comes from their being a persistent, global, advanced threat actor (see Nation-State Attackers and their Effects on Computer Security) with:
- sovereignty over the executive (eg police, trade, communications, international sharing of knowhow, compromising standards, software and chips), courts (warrants) and legislature (eg legalising spying, criminalising privacy),
- access (at source, bribing cable operators or ISPs to tap themselves, making foreign policy allowing tapping undersea cables, using satellites and ground stations which they may already have via the military, and taking ownership of choke points like switches and landing stations),
- money – (just threaten citizens with prison until they pay more tax for unlimited spying, big budget allows supercomputers (and ASIC hardware accelerators), specialisation (into directorates, geographies, protocols, databases, targets), bribery, global coverage, bringing business and academia on board, subscribing to zero day exploits and long term projects that would pay back quick enough in the private sector, such as storing encrypted texts until technology comes available to crack them), and
- scale (eg one defeat can compromise multiple targets as for example once they have a back door to encryption they don’t need to crack every cipher separately so ambitious projects become economic, and anyway big datasets help decryption).
- They can act like an organised crime gang with a crown.
- However, the state has the problems of:
- trying to collect everything in case they miss a target, which is impossible to analyse perfectly,
- hiring enough staff willing to accept the money and purpose (although increasingly bulk tasks such as hacking and translation are automated),
- being regulated,
- being tasked with pursuing state actors with sophisticated defences and lone wolves with small attack surfaces, and
- being tasked with defending prime targets like asset lists.
- Some collection is by shaping, whereby an implant on a network infrastructure device copies data to a passive collector, sometimes with selection. Implanted routers can sometimes be diverted to tailored access (CNE at GCHQ), implanted optical multiplexes tend to just be copied to passive collectors for them to do selection.
- Collection, especially since the advent of broadband, is simply too big, so it is typically trimmed down 95% by selection of targets and/or filtering of content types, eg stripping out porn.
- Intercepts are logged on the UDAQ database.
- GCHQ have decompressed satellite links using Swordfish, mapped them with Depthgauge and counted surveillance hits out of traffic with Drumroll.
- Collection is conceptually either strategic (eg bulk data) or tactical (eg covert entry or close access); sometimes it is both as if they have to hack a target the data needs to be exfiled out via network shaping using a friendly (passively collected) cable IP address or exfiled in by perhaps hacking BGP tables, or they deploy a CNE midpoint server to direct traffic to Tempora.
- All Ipsec VPN encryption keys are collected that be gotten hold of and stored on Turmoil.
- Their passive signals collection is not invisible but detection can give leads on the enemies infrastructure.
- GCQH connects to O2 Airwave at Birdlip.
- Bulk intercept is subject to only aiming to foreign communications and is subject to proportionality during analysis, but there is no blanket rule against privileged, journalistic or whistleblowers being tapped and investigated, so they are hoovered up with everyone else or even specifically targeted, and bulk acquisition of metadata covers UK residents. GCHQ says 95% of discovered hacking attempts were stopped by bulk intercept – ie rather than by CNO. About half of GCHQ reports rely on bulk intercept warrants and two thirds of those rely on content.
- Equipment interference, ie hacking, is also authorised by warrant, targeted for UK and bulk for foreign focus. However, targeted EI can be wide, and even a narrow example would be hacking all residents of a house burgled by MI5 as they do not know whose device is whose, or hacking all users of a network to stop a target realising they are singled out or to find victims and techniques of cyber attacks.
- About 20% of GCHQ reports rely on thematic EI or CNE, and a third of high value reports. GCHQ claim bulk EI is typically to identify which devices to hack more intrusively.
- Intelligence services collect bulk personal datasets, which are basically open source, purchased or government overt or covert databases, sometimes stolen, such as firearms, law enforcement, travel, commercial, communications, finance (eg Nectar), passports, electoral roll and phone book, and are mainly used by MI5 and MI6 (to link foreigners to the UK) and to a lesser extent by GCHQ to enrich other intelligence. Some include communication content or privilege. Spies have been sacked for hacking into BPDs without permission for their personal purposes. Other problems include that the BPDs can be linked to become more intrusive, to reveal everything you have earned, bought and said, everywhere you have lived and travelled, and every encounter you have had with police or the NHS. Intelligence service agencies say they need BPDs to confirm identities, identity potent spies or recruits, and for speed of investigation such as where there is no seed (eg the pool of suspects is everyone working for the olympics) or after a terror attack.
- GCHQ said in 2015 they found 141,251 new identifiers from bulk communications data, whilst MI5 applied for 20,042 warrants. However, a review of the equivalent power in USA (at 3.52) found bulk communications data never stopped a terror attack, they just contact chaining afterwards and help eliminate the USA as a home of suspects.
- Only GCHQ do bulk interception for the UK.
- GCHQ says without bulk intercept they would be stuck looking in the domain of the seed selector, and might have to risk humint or hope a foreign CSP cooperates in time.
- GCHQ and MI5 says they need bulk acquisition for fast complex searches. However, only 5% of GCHQ reports rely on bulk acquisition. MI5 use acquisition for targeting. HCHQ merge acquisition and intercept and claim analysts would not know which data was from which.
- CNO is assumed by the tribunal to involve stealing or planting data and implanting instructions.
- The UK does not do avowed bulk RI but avows GCHQ doing thematic EI more than MI5 and MI6.
- GCHQ ICTR-NE’s P2P programme is Sebacium, a keywork based suite built by Qinetiq which handles monitoring, and information operations and effects by JTRIG. Its Dirty Rat component tracks who downloads or shares particular files such as jihadi, paedo or CBRN manuals and was due to be made available to the Met. Its Plague Rat component switches search results downloads to GCHQ versions. The effects component, aka Rolling Thunder, is called Robo Rat and was due to be expanded to handle denial of service and botnet disruption.
- Five Eyes have shared traffic content via TicketWindow. That is one half of transnational DNI, the other half being SMAC metadata.
- FINNINT is stored on AAS Experiment and Luckystrike seed enrichment database, and the most sensitive such data is on Lucky Escape unselected TDI bank and travel database, typically searched by email or passport. It appears GCHQ have been able to get UK banking data via NSA’s Follow The Money and Platinum Plus programmes.
- After police break open phones at borders, at the rate of four or five people a day, at MI5 request under GCHQ ITT’s project Wildway at Merseyside National Ports Analysis Centre or Met National Ports Office, GCHQ GTAC’s Phantom Parrot tool extracts it to Lucky Strike colateral weak identifer trace database, into which it was due to be subsumed before in turn being subsumed into Looking Glass as a plugin. Targets are tricked into giving consent to content being hacked under Terrorism Act 2000 ss7-8. GCHQ then pretend they intercepted messages and found them on Dishfire, while static data is called collateral, all data is recorded under fake SIGAD UKC1164. Phone books are then matched against Corinth and Moonraker. The programme is jointly run with AGAP Target Discovery. Met liaison is via GCOs. MI5 liaison is via SFOs.
- GCHQ used to siphon off MPs emails via parliament’s Messagelabs spam filter but not have to get them from Office 365.
- Man on the side exploits can be launched afloat from four miles away using Blinddate on a laptop with 0.1W access points, antenna, RFDU and wireless adaptors , and interactive exploit up to eight miles away at 4W, with.
- GCHQ use Five Eyes’ Badass mobile ad analytics intercept to siphon off data such as Google AdMob, a mobile apps protocol exploit using GCHQ GTE’s Begal app, QFDs, Blackhole, config TDIs and Packet Processing Framework. Begal is described as an AEG (Atomic Event Generator), which is a PPF engine taking inputs from packet routers and giving outputs to event filters.
- The networks are shared as domestic telecoms are also largely international telecoms.
- Data is mainly intercepted as email, broadband or remote access.
- GCHQ’s cyber tipping software is FastFlux, whihc gets tips from Five Eyes.
- The Five Eyes keylogger is Qwerty, part of Warriorpride malware suite, called Daredevil at GCHQ, which can handle recon, rootkit detection, implant detection, file retrieval, DNS and network sniffing. Warriorpride has also implanted malware on iphones.
- CNE is either automated, interactive or human enabled (proximal, interdiction or multi stage).
- For decades the most famous programme was NSA’s Echelon which started at Bude in 1965, siphoning off Intelset comsat traffic and running it against a dictionary, whilst another site was Yakima, USA and later Sounder was added in Cyprus. Cyprus has housed spy bases at Ayios Nikolaos, Akrotiri and Troodos. The Watergate investigation revealed that GCHQ spied on USA dissidents for NSA. Echelon was condemned by the EU on 05/09/2011 and 9/11 was conveniently timed to justify mass surveillance six days later. The US army ran Bude with the Post Office since 1954 when calls were beamed by microwave from Hunters Stones.
- GCHQ share bulk billing data to government departments without a warrant under RIPA.
- We have to assume GCHQ copy NSA in interdiction, whereby they intercept shipments of routers and implant a beacon, although it is probably more of a USA project given the targets are mainly Cisco. Cisco optical network switch Sonet implants are thought to be how NSA taps USA phones via several warranted providers.
- Governments have forced providers to cooperate with warrantless tapping by threatening prosecution for insider trading if they sell shares in anticipation of losing government contracts in retaliation.
- Cables are tapped through a combination of corporate partners, foreign governments and unilateral hacks. Circuit switch and packet switch networks are intercepted via international gateway switches, endpoint gsm switches, leased internet circuit and call records, being copied from our own hardware overseas to an overseas processing centre and analysis centres and exfiled, with intercepts disguised as overt satellite sites, ie aging cold war listening posts. The take is measured in terrabits per second. GCHQ provides most of NSA’s Windstop cable taps into Turmoil, for which it is paid around ten million dollars a year. NSA’s warrant excludes Five Eyes so they would be a likely source to spy on themselves.
- Collection from embassies by covert Five Eyes staff is designated by NSA as Stateroom.
- Joint special source operations between GCHQ and NSA are designated Cleric by NSA
- Joint operations in Five Eyes against foreign spies are designated Forbidden by NSA.
- Five Eyes humint and hacking against encryption is designated as Pawleys by NSA.
- GCHQ tap even NATO member telecoms providers like in Germany.
- Providers like Microsoft put backdoors for NSA in products like Outlook, Skype and One Drive to circumvent encryption. Microsoft even have a patent for how to ghost conference VoIP.
- GCGQ send staff undercover as delegates to conferences such as for climate change as they did in Mexico in 2010.
- GCHQ have integrees such as from MTI Access team working embedded in providers such as Vodafone as paid partners. MTI (Mastering the Internet) was built by Lockheed and Detica.
- GCHQ have partner cable taps at Whitesands Bay, Bude, Highbridge, Pottington, Goonhilly, Porthcurno, Oxwhich Bay, Skewjack Farm (Sennen, Flag cable, ‘Nigella’ tapping Porthcurno & Sennan Cove), Sennan Cove, Southport, Hollyhead, Lowestoft, Thorpness, Aldeburgh, Broadstairs, St Margarets Bay, Cheriton, Brighton, Dunnet Bay, Pervensey Bay, Hunmanby, Scarborough, Winterton-on-Sea, Redcar.
- GCHQ have access to NSA’s Thieving Magpie and Homing Pigeon to hoover up inflight call (social media, webmail, bit torrent, media, VoIP, travel apps), subscriber and handset data via Southwinds INMARSAT BGAN satellite terminals onto RESTful web for Five Eyes, allowing tracking every two minutes.
- GCHQ piggybacks on NSA’s Dishfire SMS database to spy on UK citizens for contacts, locations, SIM changes, payments, passwords, bookings and border crossings.
- Optic Nerve collected Yahoo webcam screenshots every five minutes from the whole country, 7% of which were camming, including teens.
- Quantumtheory is a mostly low latency protocol injection man on the side attack designed for hacking visitors to terror websites, receiving tips when targets request target IPs, triggering delivery of a redirect by a Straightbizarre ‘shooter’ implant on a hijacked computer, programmed by FelonoyCrowbar GUI using a deployed node document and XML config, to a fake page on a GCHQ mirror on command of Turbine (remote agent active mission logic) via Surplushanger (high to low) and Hangersurplus (low to high) diodes (not used by GCHQ) which use high proxies to convert to Chimneypool messages sent on IslandTransport, low proxies to talk to Chimneypool and Friezeramp, and a high to low packager. For NSA at least, Chimneypool comms are run by Genie network configuration centre via Middleman which has web sniper gateways between then and shooters. It uses Turmoil passive sensor, Island Transport corporate messaging fabric (using Island Hideaway encryption), Daredevil shooter, Quantuminsert HTML redirect, Quantumsky HTML/TCP resets by RST packet spoofing, Quantumbot idle IRC botnet hijacker, Quantumbiscuit high latency HTML cookie redirect for identifying opaque users especially from Yahoo email addresses converted to L-cookies, QuantumDNS DNS hijacking by A Record targeting single hosts or caching nameservers, Quantumcopper download disrupter, Quantummush span exploit, Quantumspim instant messenger XMPP, Quantumsqueel MySQL injector, Quantumsquirrel IP simulator, Quantumhand Facebook hacker, Quantumphantom IP enslaver, Quantumdirk webmail poll injector.
- Abroad, content and communications data is intercepted by GCHQ’s SigMod with fibre optics going into Global Telecoms Exploitation team and out through NSA’s Distillery streaming analytics which outputs answers without storing data (sold commercially as IBM Infosphere Streams, written in SPL with toolkits stored in MadForge), which had a Graph Analytics Toolkit, to the Splunk dashboard, with social media analytics contexted by Airwolf metadata, whilst within the UK bulk intercepts are done by GCHQ’s NTAC (created in 2001 as GTAC and reported to Director GCHQ from 01/04/2006 and subsumed into GCHQ Ops from 01/07/2008, with some avowed Home Office staff for court cases, who handle legacy intercepts, warrants, decryption and processing, runs about 11,000 taps a day mainly from telecoms providers via the Bouncer, Canley, Catsup (airline booking taps), Condone, Hooch and Zamensis programmes feeding into MI5’s DigInt (counter terror web intercept) and Milkwhite target (IP address) enrichment service (originally via SOCA’s Internet Data Unit for law enforcement and MI5’s A8 Digint Identification Team), but also NHS data, with 100-150 staff and over £40M budget, with Operations doing forensics and Technical doing intercepts, and are based in MI5 at Thames House (with a secret disaster recovery site), the sites named Hence and Funfair, with a programme team also at Cheltenham to where data is pumped into databases like those for events (Salamanca for VoIP, Haustorium for C2C, Sambock for geo) or content (VLST for telephony events, B3M for VoIP and Samdyce for SMS, liaising with Home Office Communication Capabilities Directorate). Output goes to processing on Terrain at Benhall or Hotline. NTAC claim GCHQ have got 60% of counter terror special source from them. NTAC is an avowed agency as far as forensics goes. The way NTAC works is the intelligence analyst identifies a target and asks for a feasibility survey to be conducted on Terrain intercept processing system by Farndale signals analysts, then the tasking manager (eg GCHQ Preston ops) requests the target to be added to a warrant schedule, then the Home Office give law enforcement a warrant, usually for a packet switched line, then law enforcement ‘enable’ the intercept by telling the communication service provider (‘CSP’) who to tap, and then the CSP ‘provision’ the data to NTAC through optical cable and an NHIS software diode (one way valve to air gap networks of differing security, designed by TPS) if unaccredited or straight to a collection domain if Secret-accredited, or HMGCC via mediation units for mobile networks, then on to an NHIS router on to either cyber research or signals development at GCHQ GTE Survey or Terrain cluster for collection processing, which passes it on to law enforcement via a collection or delivery domain, for example as a stream to GCHQ via diodes for security (to Content Enhancement if processed data), supervised by a collection manager such as GSOC and surveyed by a signals development analyst, then the intelligence analyst assesses the take and if useful asks to migrate the stream from survey to collection. The stream router has been provided by LogicaCMG. The PDO diode is a Sybard diode with Apache server. The input diodes connect to CSPs and the output diodes connect to NHIS router via GCNet. The diodes are input and output proxies to protocol data along a one way cable. This can be monitored with something like HP Openview. The intelligence analyst will initially use the first data to develop targets on Blacknight (before the advent of broadband anyway) from the Cadence dictionary while the signals development analyst will see if they can filter by technology. Filters are recorded on Corinth, Trafficmaster or Tacho and may have been plugged into Fast Grok scanning engine. They also get Terrain computer-to-computer (‘C2C’) data from GCHQ. A former head is David Johnston, ex GCHQ and ex Met. NTAC used to be described as part of the Home Office Crime Reduction and Community Safety group and within NTAC sat the ‘Forensic Computing Team (Stored Data)’. It all sounded innocuous like a cupboard in a basement somewhere where the odd paedo’s laptop could be cracked, as part of an operation that sounded like some sort of cuddly camera safety partnership running speed cameras. Agencies would go via their principle points of contact (‘PPoC’) to request taps or hacks. NTAC also runs legacy circuit switched and line access intercepts under Boxter, Marmian and Gentian programmes. NTAC intercepts are not only against suspects but anybody for penetration research by GCHQ, which used to be done by CESG but presumably now by NCSC. GCHQ used to be drafted in to intercept leased lines for NTAC. NTAC have intercepted emails by ordering CSPs to clone email addresses. NTAC try to get data out to agencies in MIME/CCDF format through their Processed Data Output service.
- NTAC is part of the Home Office but run by GCHQ after it moved from MI5, within the Office for Security and Counter Terrorism (‘OSCT’, running CONTEST, Research Information & Communications Unit (‘RICU’) anti-jihad pysops such as radio plays such as Divided We Fall, leaflet drops, fake civil society websites like ThisIsWoke and Ummahsonic delivered by outsourcers like Zinc Network, fake Al Jazeera videos, ghostwritten books like The Islamist and PAs by influencer such as Sarah Khan with £40M budget and 70 staff, COBRA terror crisis response and interfacing MI5 to the Home Secretary), sitting under the Communications Data Lawful Intercept (‘CDLI’) service delivery partnership with embed NTAC and NCA staff alongside the National Communications Data Service (‘NCDS’, with applications for workflow, case management, and data mediation and management, provided over the cloud by Leidos with subcontracts to CGI, BAE, PA Consulting and Roke Manor Research, being replatformed in 2021 to Agile Data Retention and Disclosure Services (‘ARDS’) via AWS on the cloud) and Communications Capability Unit (‘CCU’) in Hoime Office. The Threats & Risk Assessment, Capability Exploration & Research (‘TRACER’) also sits under CDLI but within the NCA, acting as a clearing house for law enforcement and intelligence looking for new criminal telecoms and ways around them.
- CDLI benefits from Accelerated Capability Environment (‘ACE’), a consortium of over 230 companies and universities, collaborating over Vivace, led by Qinetiq, meeting at Tintagel House, sponsored by the Home Office, who help government hack data in return for some spook fairy dust. It runs Impact Lab, Collab Lab (hosts the National Security Technology & Innovation Exchange (‘NSTIx’) and Data Investigation and Collaboration Environment (‘DICE’). It also automated the Child Abuse Image Database (‘CAID’) to identify, classify and match images.
- OSCT also runs the Joint Security & Resilience Centre (‘JSaRC’), which asks the private sector to help.
- OSCT’s budget is thought to be £1bn with 900 staff, working with 22 other bodies.
- Preston filters out about 95% of intercepted data using Blacknight.
- Echelon was run by GCHQ and funded by NSA using Comsat antenna, with the UK ones called Snick (Oman), Sounder (Cyprus) and Carboy (Bude), and NSA running one in UK called Moonpenny (Menwith Hill at Harrogate).
- Having been tasked with a target, an analyst reports on the target’s data. However, whilst countries are sitting targets, criminals may be unknown, so target discovery and development requires a target and eventually a query and thus more data sniffing, starting with an ID from a spy and working out to find their neighbourhood of contacts, and sometimes there is no starting point and thus no target and no query, so to find selectors MOs (behaviour patterns such as pay phones and burner phones) are used for known queries with unknown targets and anomaly detection is used for unknown targets with unknown queries. Such patterns were invented to spy on G20 delegates, repurposed for counter terror and then adopted for military intelligence. Queries can then be used for target tracking.
- Lawful intercept technology can be misused by rogue insiders at the CSP or maybe even hackers, as happened in the Athens Affair in 2005.
- Although more of a risk for MI5 who do more targeted collection, GCHQ train to consider risks such as capabilities or hacks being compromised by passive SIGINT, security or leaks. They worry about forgetting to delete logs and email read status the same as any other hacker, but carry the extra risk of relying on enabling commercial partners, sometimes chains of them.
- GCHQ use bot herding for DDoD, spam and collection through IRC, P2P and HTTP. They take over the ‘C2’ command & control nodes that sit below the master herder, and for cyber defence may insert a quarantine engine and bot prison under the master herder. GCHQ midpoint collections are a main finder of botnets. They use Xkeyscore to find exploitable bots, task Turmoil to watch for traffic from them and then task Turbine to generate a man on the side command packet telling the victim to download an executable, but subject to race condition. GCHQ’s Quantumbot uses Turmoil passive tipping to Incensor, Turbine interaction and man on the side snipers from Menwith Hill. GCHQ botnets are sometimes used for active exploits, disposable unattributable attack nodes and network analysis vantage points, but have to avoid bleeding edge techniques to not look like a state actor. Encrypted bots may be attacked with Tumoil reinjectrion flow and P2P may be tracked using Turmoil FastFlux.
- JTRIG work with SIGINT Development and CNE. They are part of Joint Electronic Attack Cell alongside EITT and EA Threat Team.
- Technologies that caused problems for NSA as at 2012 included Tails, Tor and Truecrypt and to a lesser extent Teamviewer, Join.me, LaplinkGold, Web.de, Cspace, Redphone, Muslima, Purematrimony.com and Zemana anti keylogger. Encrypted webmail and messenging and RATs have been a problem.
- NTAC staff, such as Ian Cooper, Mark Shepherd and Mark Canterbury, and probably Tony Youel, sat on ETSI committees, writing standards for interception and data retention, eg for mobiles. These allow authorised organisation to order communications service providers to disclose dozens of data fields such as subscribers, calls, geolocation, PUKs, handsets, SIMs, bank details, including all a customer’s MACs and IMEIs.
- Hacking has been done by GCHQ’s Network Analysis Centre (‘NAC’), set up by JTRIG, GTE and GTAC, using programmes called Cerberus, Stargate, Mugshot, Quantum and Wharfrat, in five pods (‘NACs’) of ten workstations with non-attributable internet, run by an operations manager supervising network analysts from Cheltenham, Bude and Cyprus, a GTAC data miner, an open source specialist (for network analysis), JTRIG analysts from Cheltenham & Bude, CNE operators from Cheltenham and Scarborough, a VPN crypt expert, an EREPO expert, a protocol analyst, a production tasking coordinator and trainee operations managers, with JTRIG desktops and tools including Highnote CNE toolsuite, Copperhead CNE attack box, Nexus MI6 desktop, Caddis MI5 desktop, Jedi unattributable internet public network interfaces (under RIPA directed surveillance regime) and E-beam, triple NRT tipping 20″ screens, foot pedals (emergency kill switches?), KVM switches, GC Desk mail browser, a virtual whiteboard and a 65″ projector. Attacks have included mobile billing clearing houses (Operation Whylekey, eg against Mach), mobile gateways (Operation Interaction) and GPRS roaming exchanges (Operation Socialist, eg Belgacom for man in the middle attacks on roaming smartphones, penetrated via IR21 (GSMA roaming database) extraction, LinkedIn & Slashdot ‘shots’ (infected emails, 1 in 20 users reply to malware emails and in 1 in 3 of those are exploited) and Quantum inserts (probably using Regin malware loader, available to download) and Woodcutter programmes). Ruses include content delivery, which is infected email attachments that trick recipients into visiting exploitation sites, masquerades, which is impersonating users in forums etc using stolen logins, router ops (‘EREPO’ passive collection), which is taking over admin accounts, and remote access, implants, which is compromising operating systems, phones and hardware. There is some joint working with second parties like MI5 and MI6, with whom they deconflict IP addresses. A GCHQ pod uncannily like a NAC was filmed for a clip in a documentary, screenshot above. Quantum implants are deployed by the million via Turbine, posing as a Facebook server or using malware spam to hack webcams or secretly blacklist sites for a user or sabotage downloads. Telephony is targeted from Salamanca data mining and emails by cookies and Radius data, and then spoofed using Infinite Curvature or Mountain Slope. They see the spectrum of intrusiveness of effects ranging from call bombing and wifi denial of service, through email & SMS spoofing, hotel attacks, psyops, maritime cyber and internet routing, to critical infrastructure. They analyse targets with template targeting, starting with the target space of target, infrastructure and technology, then look at the opportunity space of vulnerabilities, capabilities, access and plan delivery. They may then use Hotwire BGP or MPLS network effects.
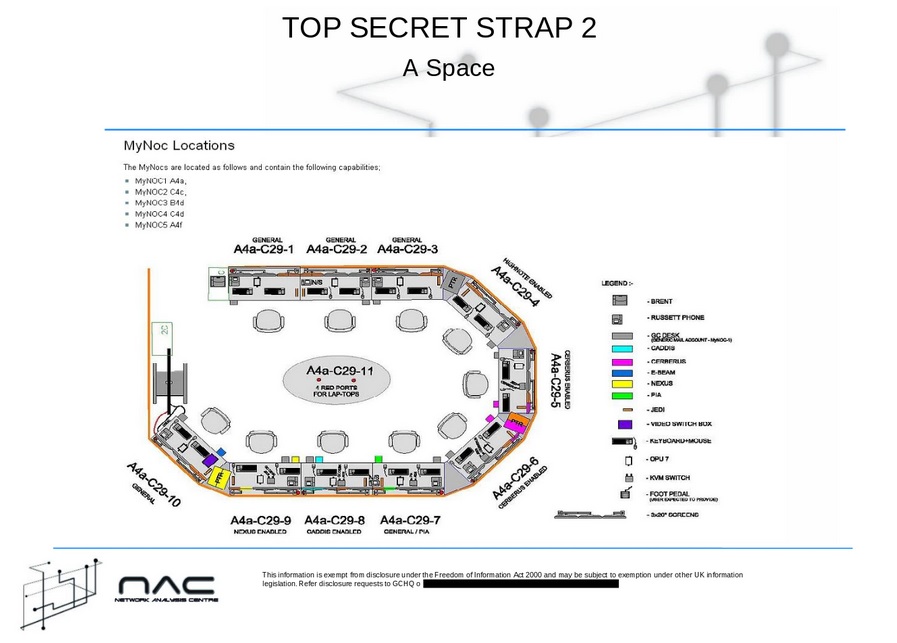

Analysis
Background
- After targeting comes understanding or enrichment, followed by an action such as a report or arrest.
- Analysis is made difficult by volume, velocity and variety, because there are many haystacks travelling at the speed of light.
- AI is increasingly sought to be used to counter hackers and psyops. There is probably more talk than action. Often what is called AI is actually just a formula. But the MoD hired the Alan Turing Institute to advise on using AI for automated hacking and cyber defence.
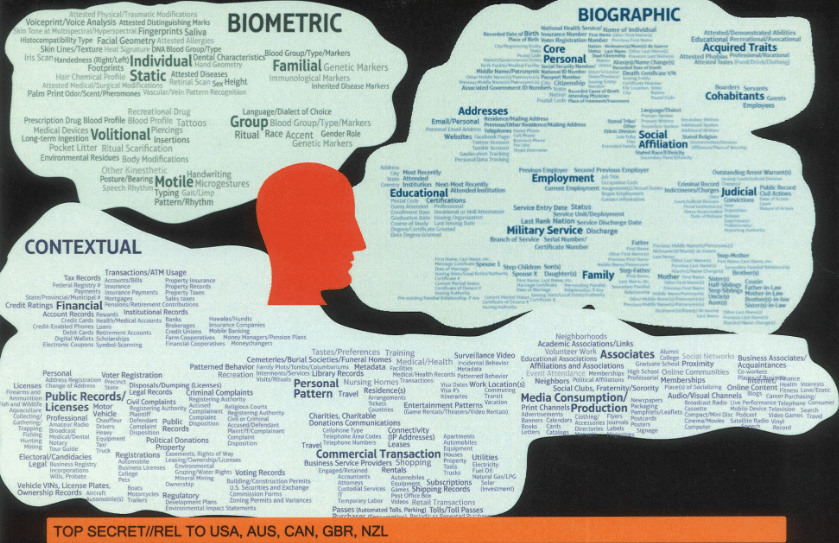
UKIC
- In terms of processing, in the UK MI5 handle national security whilst law enforcement and HMRC handle crime and economy where they feel able, calling in GCHQ if not and sometimes SIS and NTAC, whereas abroad SIS and MI6 both process data for any purpose, with SIS and MoD helping GCHQ with targeted temporary intercepts overseas.
Tools
- Their inhouse intranet was called GCWiki which is rated up to STRAP1.
- GCHQ have used BBN Byblos for automated speech translation.
- GCHQ also run:
- Crouching Squirrel botnet detection via data mining using approximate subgraph isomorphism,
- Chart Breaker email network identifier based on Jung Java graph framework,
- Blazing Saddles database of web profiles allowing discovery of unknown accounts for a user from communications data and content such as metadata and Google map searches (Marbled Gecko),
- Harbour Pilot enriched metadata database,
- Black Hole database of dumped bulk metadata (eg millions of Twitter events daily),
- Social Anthropoid (replacing Social Animal (which tracked interaction with files and users), Haustorium and Salamanca) creating social media user profiles on a database of text, email and social media communications data,
- social media cookies to ID users:
- GCHQ uses cookies, IDs, IPs, keys and MACs from Windows, social media, webmail, devices, ciphers and networks,
- the Mutant Broth database had 18 billion rows in 2008, and is used for example to check traffic for five hours before and after a suspicious FFU download,
- Auto Assoc is a cookie & technology matcher to pair users and machines,
- Enhanced Mutant Broth is a cookie sniffer for locations and devices,
- HardAssoc finds selectors from cookies for phone and chat,
- HRMap tracks hostnames of hosts and referrers to track sequential website visits – to stop which you need to type URLs, bookmark them or set your browser not to send referrers,
- Karma Police matches cookies to computers, times and websites and find other websites visited by a browser and IP address,
- Social Anthropoid tracks C2C comms and social events (who communicates with whom via a locator such as an IP address or mast) and set alerts for suspicious searches or map views,
- Infinite Monkeys tracks forum posters,
- Memory Hole tracks searches,
- Awkward Turtle tracks what other sites visitors like),
- voice recognition on software from NSA R64 and hardware codenamed Ghostmachine with Distillery process provisioning and voice analytics, to identify voice, gender, dialect, keywords and attempts at disguise through modulation, which can be done in real time by postcode, and used to rely on sharing NSA’s Nucleon database (NSA used Nexidia‘s Nexminer, GCHQ’s equivalent was B3M) and GCHQ’s Rosecross tool later replaced with NSA’s Hotzone integrated with GCHQ’s Monte Vista, and
- cloud projects like JCE and TINT,
- Grinning Roach and Pirate Carebear SIGINT event visualisers for plotting pattern of life,
- Flying Pig TLD/SSL knowledge base (with weekly updates of 20 billion events by certificate metadata, server IP, client IP, network range, typically for finding malicious traffic and foreign spies eg Russians exfiling from hacked companies) and Hush Puppy private network traffic attribution tool (matching private and public cookies such as Yahoo t-cookies in special sources and Comsat, typically flushing out secret government networks) as cloud analytics for bulk unselected data within ICTR network exploitation team,
- Used to run Anticrisis Girl on Matamo open source web analytics, tracking visitors to sites like Wikileaks and Pirate Bay.
- Some queries are stored in Palentir’s Raptor federator server, the other server being Versioning. Federator would have been used to map to graphs from Broad Oak, Haustorium and Salamanca.
- Palantir investigation enricher helper, analyst workspace and visualiser. Palantir are a CIA spinoff big data company, who originally worried GCHQ as being too talkative and expensive, but GCHQ caved in and bought their help as they were so far ahead of spooks in data analysis. Palantir are also used by USA and Australia signals intelligence. Palantir defaults to Microsoft active directory, and its back end is a semantic graph backed by Oracle with map reduce architecture. They charge per core. Palantir ran the data analysis for NHS bed occupancy, PPE distribution and vaccine rollout.
- Back around 2010 GCHQ researchers could borrow clusters with 5,216 cores and about 20TB RAM.
- Analysts have to include a Butler intelligence source descriptor on reports, including access, identity and reliability, in an effort to avoid future Iraq-style fiascos.
- GCHQ have worked on joint experiments with NSA on Voice RT voice recognition, which picks up speaker, language, gender and keywords. This used to rely on Tibo software, now replaced with Distillery running on Ghostmachine hardware with R64 voice analytics.
- Much use is made of Hadoop, written in Java, for batch analytic clusters on Apache cloud storing up to 32 trillion events, and Apache Accumolo, with GCHQ trained by Cloudera, the main cluster being at Cheltenham being Sunstorm and at Bude being Hager Awel (a Cornish storm), with user directories being at least 2TB each. One Hadoop cluster was called Gold Mine.
Collaboration
- GCHQ jointly run the Centre for Law Enforcement Audio Research with MI5, Home Office, NCA and HMGCC.
- GCHQ supply partners with data via VAIL web user interface and brokering.
- Five Eyes set up intelligence sharing deals with countries with aligned interests if they need tipoffs (‘Indications and Warnings’). Partners can bring access to telecoms, knowledge of targets, language, while Five Eyes bring technology.
- Communications data (‘metadata’ or ‘secondary data’) and lawful intercept are processed by NTAC’s Communications Capability Development programme (formerly Internet Modernisation Programme, built by EDS) (which runs EIS) and content by NTAC’s CTIP, while targeted intercepts are requested by law enforcement (HMRC, police (NCA & special branch), MoD and intelligence) and MI5 at the rate of thousands a year per telecoms provider.
- GCHQ handles strategic and tactical overseas metadata and content collection, with MI6 and MoD helping on some tactical tasks. Their EIS and Home Office Communications Capability Development programme also run domestic metadata collection on behalf of law enforcement and GCHQ run NTAC within MI5 to collect domestic content for law enforcement. Exploitation of foreign collections is shared with MI6. Exploitation of domestic collections about foreign threats is led by MI5 but assisted by GCHQ. GCHQ help law enforcement domestically, with MI6 helping overseas and NTAC helping domestically.
- In theory MI5 handle spying in the UK but can ask GCHQ for help under their auspices of an MI5 warrant for UK interception, whereas GCHQ run all overseas signals for MI6.
- GCHQ also work with SIS, MoD Strategic Command and DSTL in the National Cyber Force, which is the latest incarnation of National Offensive Cyber following years of turf wars.
- GCHQ maintain a joint collaborative environment for experiments with NSA called Innov8.
Staff
- One team is MCR maths and crypt research.
- Managers are trained in supervising neurodiverse staff.
- Whilst GCHQ have illegally collected bulk data on the UK population and enjoy light touch regulation, if it was not for them we would be speaking German.
- Many of their staff could walk out today and double their money in a private sector cyber firm, one was murdered for his troubles recently, and some are sent to the front line on only Met constable money.
- Some are so clever it would make your nose bleed, and you want them because in terms of signals they are all that stands between Ivan overthrowing your government and you, between CCP blowing up your nearest power station and you, between Pakistan selling nukes to terrorists and you, between jihadis blowing up your troops with IEDs and you, between new enemy weapons and you, and between paedo rings and your kids. You just have to hope someone would whistleblow if it got out of hand.
- Whereas they used to get enough staff from university tutors, now due to expansion they have to run constant recruitment campaigns for geeks and conveniently have a tv sitcom, David Schwimmer’s ‘Intelligence’, doubtlessly wangled by GCHQ through Sky, who are a (paid?) corporate special source.
- Numerous former staff have outed themselves, such as e-crime consultant Chris Sundt and security consultants Dr Bob Nowill, John Davies, Matt Tait (the Trump Russian collusion hoaxer who deleted his account), Mike Beck, Dave Palmer (Mike’s former boss), Sally Walker, Cath Goulding, Andrew France, John Richardson, Neil Sinclair, Kevin Tebbitt, and others publish letters such as Nick Negus (spectrum manager), Dr Jamie Saunders and Neil Kempsom (director engineering & technology). NCSC avowed names include Lindy Cameron (CEO, ex-‘ ‘DiFID’, FCO and RCDS, ie MI6), Dr Ian Levy (GCHQ, NCSC technical director resilience), Paul Chichester (GCHQ, NCSC director operations), Chris Ensor (GCHQ CESG (UK’s NTAIA), NCSC deputy director skills), Deborah Petterson (NCSC director private CNI), Eleanor Fairford (NCSC deputy director incident management), Jacqui Chard (GCHQ, NCSC deputy director defence).
Capabilities
- Not all capabilities map to known codenames or were leaked by Snowden, some leaks were of intended capabilities which one presumes have been achieved by now, and some capabilities exist in the private sector or abroad or can be discerned from academia or the telecoms industry. So any capability not in the taxonomy above is listed below.
- Their capabilities are instructive in assessing risks from other threat actors and from a government going rogue.
- Their strength is the skills, technology and partnerships allowed by government funding and regulation.
- Even if you had the money you would struggle to buy the kit and get the cooperation they have.
- You don’t have your own sensitive relationship team, so cannot just ring up CSC, CGI, HP, Raytheon, Carillion, Logica, Lockheed Martin, BAE, Detica (supplied Remit temporal graph Chains analytic algorithm – later updated by Primetime for activity levels streaming, and Mamba visual analytics for network graphs), Verizon, Vodafone, GTT, Viatel, G4S, CenturyLink, IBM, BT, Cisco, PA Consulting and Juniper and ask them to run a hacking HQ like they do.
- And however much of a geek you are, you are not a CNE expert, linguist, researcher, engineer, mathematician, chemist, physicist, computer scientist, infrastructure engineer, intelligence analyst, firmware designer, system architect, AI expert, data scientist, cryptographer AND security engineer with OOD, NoSQL, Linux, Perl, Python, C++, Cloudbase and Hadoop.
Known
- Buy and use commercial off the shelf tools such as GCHQ’s Bad Decision package of Macchanger, Wireshark, Nmap and Ettercap.
- Read screens using rasters or emissions.
- Hack your devices, such as webcams, to circumvent some security and use face recognition and voice recognition.
- Trace cloned phones via Golden Axe database.
- Trace location in Public Anemone database by matching map searches.
- Reverse engineer software to find out how to hack it (eg decrypt files, unmask and spoof forum users, divert router traffic, infect Office or Acrobat files and circumvent anti virus software). Findings are annotated in IDA Pro.
- Crack encryption for NTAC law enforcement such as EDataDisk and CrypticDisk.
- Hack hosting control panels like CPanel used by GoDaddy for example.
- Implant choke points to redirect traffic to GCHQ servers.
- Deanonymise anonymisers by studying them, then deploying XKS fingerprints and static IP mappings.
- Turn on mobile microphones with Nosey Smurf, and control power on a mobile with Dreamy Smurf, and extract geolocation from a mobile with Tracker Smurf, plus kernal stealth and file retrieval programmes.
- Extract keys from Microsoft TPM chips and edit BIOS without Bitlocker knowing.
- Hack some chips via their Technical Enabling Covert Access Product Centre’s TEA Reverse Engineering team, who specialise in covert access, mobiles and crypt, and work with PTD on hacking, and have a lab with tools from Agilant, HP and LeCroy. TEA supply MI6 with gadgets and TECA Ops techies in the field.
- Deanonymise Tor:
- Epic Fail (for cookies of ‘dumb users’ between Tor sessions),
- Exploit Torbutton and TBB software with Shortsheet etc,
- Persistent cookies after Tor sessions,
- Low latency (Quickant matching when target is online in a country),
- Inserting nodes (eg taking over IXPs or ASs, Newtons Cradle for circuit reconstruction, and timed packet to get IPs, shaping traffic to GCHQ nodes or to private GCHQ Tor eg via denial of service or control ports, traffic staining with Mullanise, forced connection outside Tor, (slow) node flooding),
- Timing attack on hacked server,
- Writing browser addon exploits,
- Exposing cookies via redirects to webmail,
- Tracing hidden services using referrer IDs with Onionbreath, eliminating exclude nodes from a rendezvous point, and fingerprinting with Build ID dates,
- Another possibility is obviously cracking OpenSSL or forging RSA X509 certificates to circumvent TLS but still leaving onion layers intact which can be attacked via authoritative directory servers.
- Deanonymisation likely to be a fraction of users and not necessarily individual targets, but GCHQ only need to find the IP once.
- GCHQ had a joint NSA tor project called Remation on AWS.
- Ronin programme monitors nodes.
- Tor circuits are identified by looking for Tor SSL certificates, which are known.
- Foxacid javascript iframe redirector.
- Potent Probables programme looks for proxies.
- Hack using tools such as Syringe, Helmage and Porridge.
- Hack foreign military plane and drone video.
- Bug Inmarsat phones on planes.
- Use Google cookies to identify targets.
- Scan for CBRN websites.
- Infect webmail draft boxes.
- Download private facebook photos.
- Identify terror videos by logos.
- Spot if you searched for related terms within a timeframe.
- Via their Mobile Handset Exploit Team, steal encryption ki keys from SIM manufacturers such as Gemalto (which match SIMs to network’s Home Location Registers), store them in GCHQ’s UDAQ C2C database run by TDSD team, and hack their customer and billing database and intercept and decrypt keys from networks and manufacturers. The social engineering is done by JTRIG.
- Circumvent encryption using stolen, bought or warranted master keys and backdoors in products such as Juniper chips used by VPNs and 4G phones, potentially with the help of NSA’s Commercial Solutions Center, encryption backdoors include implanted bugs in code that ‘accidentally’ reduce randomness of keys allowing decryption from only 48Kb of text.
- Implant spyware in app stores.
- Tap international cables with Endace probes.
- Trace who listens to internet radio.
- Hack PCs via an Office doc.
- Hack Blackberrys, and iphones (eg NSA have Dropoutjeep to take control of iphones).
- Set up fake internet cafes at international conferences with keyloggers (to steal logins) and email interception.
- Spot particular files being sent using Signature Knowledge Base hashes on Black Hole and QFD.
- Deanonymise bitcoin if you are careless during purchasing, as they can look for MAC and IP addresses.
- Infiltrate online games with fake avatars to spot terrorists using them to communicate with file transfer, chat and VoIP or recruit, train, plan attacks or buy anonymously, and to help network development, and launch psyops in existing games or launch government-designed games.
- Hack hard drive firmware, assuming they have a version of NSA’s Iratemonk.
- Hack routers, eg NSA have Banaglee and Jetplow to put a back door in Cisco routers, which can involve reflashing BIOS, likewise for Huawei and Juniper firewalls, the main interest being ISPs. This allows adding credentials, rerouting (eg to passive collection in Pakistan), packet capture, VPN encryption degradation and implanting compromised GCHQ versions of operating systems.
- Tamper with hardware in the post to you, eg insert chips like NSA’s Howlermonkey range.
- Tamper with hardware in premises, eg install NSA’s Cottonmouth RF transmitter to leak from USB cables or Firewalk to leak Ethernet.
- Implant a tool like NSA’s Sombreknave software to create a secret wifi connection out of an airgapped computer
- Implant to a SIM’s STK via OTA to extract SMS, call logs and phonebook via SMS using a tool like NSA’s Gopherset, or location via NSA’s Monkeycalendar.
- Hide something like NSA’s Candygram GSM tripwires to send SMS alerts when targeted mobiles come near.
- Con a target into using a mobile implanted with something like NSA’s Picasso , which sends SMS detailing target metadata and even voice to a laptop and mobile.
- Hide something like NSA’s Photoanglo, or Ragemaster hidden in VGA ferrite, to siphon off video cable data by bouncing microwaves off it, or Surleyspawn for keyboard, costing about £30.
- Read screens remotely using something like NSA’s Viewplate.
- Bug rooms with RF retroreflectors, like NSA’s Loudauto, that don’t need much battery and are scanned by radar.
- Hack a PC from up to eight miles away with a wifi packet injector such as NSA’s Nightstand.
- Inject an iframe into a shared webmail draft.
- Hack an internet connection with XSS or spam phishing, although a bit old fashioned now and users are too savvy and it is too easy to rumble.
- Presumably, like Canada’s CSEC, set up wifi traps such as at airports, and then track recorded device users across a city by wifi.
- Launch DDoS attacks, eg Rolling Thunder against Anonymous, who they also entrapped with agents provocateurs on forums and scared off 80% of users.
- Disrupt enemies by encrypting their machine with Ambassadors Reception.
- Download files to a machine using something like NSA’s Validator.
Presumed
- GCHQ presumably can do what NSA looked at which is:
- remotely bricking network cards,
- zeroising hard drives,
- erase server BIOS,
- create secret partition on drive,
- hack network cards without using the operating system,
- try to put back doors in Apple xcode for apps to disable security, copy data to listening post and impersonate developers, and force OS X updater to download a keylogger,
- identify couriers by analysing clusters of extra travel with mobiles linked to targets coming and going from a UCELLID polygon, with cotravellers or mobile power down, handset swapping or incoming calls only, as NSA Skynet did with Al Qaeda,
- as a member of Network Tradework Advancement Team, turn app stores into a man in the middle attack, with techniques stored on Crafty Shack, initially aimed at putting psyops onto mobiles to influence protests in the middle east.
Internet of things
- Before you even look at your devices remember that Ring doorbells are Amazon spyware which allows them to view all videos via an admin account, even you never upload them on Neighbours app, and police have been paying citizens to fit them.
PCs
- Learn how to harden your data security with throwaway email accounts, secure phones, Tor, VPN and secure email and secure messaging. The Hated One has done a good series of Youtube videos.
- Use the latest widely tested version of operating system.
- Use a security suite such as a firewall.
- Use a browser and pdf reader with sandboxing feature.
- Keep software up to date.
- Enable full disk encryption.
- Be careful where you download from.
- Be careful what permissions you give software.
- Only connect to your ISP’s router via your own router.
- Disable tunneling.
- Look for a router with firewall capability. Enable NAT. Disable remote configuration.
- For wifi avoid WEP and go for at least WPA2.
- Put strong passwords on all network devices even printers.
- Use strong passwords for all accounts, including entertainment like Prime, and disconnect devices when not in use.
- Only log in to admin account for installations. Use an account without privileges day to day.
- Check PrismBreak for suggestions of safer software.
- Try not to use Intel or AMD chips, as they may have NSA backdoors. That unfortunately locks you out of pretty much the whole market, so your practical solution is to keep adversaries out of your internet and buy your CPU anonymously, or stump up for a Purism Librem laptop – but even that security hardened PC runs on Intel chips.
- Do not use monitors with cameras or microphones as these can be hacked with physical access.
- Beware unexpected dongles like the Key Croc which can take over your keyboard,
- or the SharkJack or Screen Crab.
- Beware strangers in the house as there are dangerous gadgets out there, like Bash Bunny.
- Do not use ‘internet of things’ devices like Assistant or Alexa as these can be hacked and those with microphones are always listening in and can be spoofed with lasers or broadcast wake words and are recorded at HQ.
- Don’t use Windows, it has an NSA backdoor and can more easily compromise virtual machines, so use Linux instead, although to be fair any operating system can potentially be hacked in a hypervisor attack and thus open the door to a virtual machine. In fact, as Microsoft is an NSA partner, avoid all their software. The same goes for Apple, Skype, Youtube, Facebook and Google.
- Prevent apps like Twitter spying on your opinions to decide whether to censor you by sandboxing it in a separate browser – other than Chrome, Opera or Safari – which can be defingerprinted, such as Icecat or Firefox set to never remember history, by using the extensions uBlock Origin, Decentraleyes, Cookie Autodelete, HTTPS Everywhere (blocks unencrypted pages) and uMatrix. Use Icecat for Twitter and Firefox for browsing. Brave, Palemoon and Waterfox are other privacy browsers you can use to create further such compartments.
- Likewise, Facebook tracks you unless you use a separate browser and session and delete its cookies after each session. Ideally delete your account and stop using this NSA spyware, which tracks even non-user contacts of users, and hacks you and sells your data.
- Defingerprinting removes metadata from your PC but not your IP address. For that you need new Tor browser sessions for each site and a burner phone to create accounts such as anonymous Twitter.
- Close your browser after each purpose of use and delete history and cookies. The way around this is to use Qubes browser, which compartmentalises browsing but needs technical minded users. An easier, slightly less secure approach is to use separate Firefox profiles. Your work, social media and private browsing profiles each need their own burner phone number and email address. Work and social media should be done in privacy hardened browsers outside Tor, so as not to blow your cover in Tor for private activity.
- Only use each browser for one purpose so, for example, work sites never see your personal sites.
- Choose purchases on Tor, then copy the link to a privacy hardened browser to buy, so you do not match your bank details to Tor.
- Protect Firefox from java hacks with Noscript.
- Only log in as admin when you need to install something.
- Keep backups.
- To securely delete files reformat with overwrite.
- Avoid dodgy pages, links and attachments.
- Prevent physical access to sockets and drives, otherwise a hacker could take over by plugging in something like a Teensy.
- Consider Tails as an operating system. You can use a machine anonymously by booting from a Tails USB which browses via Tor. However, if you use it within a virtual machine then the host operating system could compromise it.
- Install Veracrypt.
- Consider air-gapping your computer by disconnecting from the internet and only moving files via USB.
- Consider only storing sensitive files on encrypted USBs in a safe.
- Be aware that states can circumvent https by downgrading you to port 25 or using their root certificate. The only even partial protection against rogue governments abusing certificates is certificate transparency and public key pinning.
- Be aware that states may have persuaded encrypted messenging platforms to allow ghost conferencing, invisibly adding spooks to your chat via a secret extra public key to circumvent encryption.
- Consider running your own email server such as Helm. Then some of the only ways in would be the manufacturer spoofing your DNS or pushing you a malicious update.
- To destroy a computer you need to grind all chips to dust (as some have secret memories) and degauss what is left, which is the Five Eyes sanitisation protocol.
- Ideally not just keep work and personal browsing separate, but via separate accounts and ideally on separate machines.
- Restrict confidential use to your most secure machine via ethernet, as devices on wifi or used by your kids will be more likely riddled with malware.
- Do not store on the cloud anything you do not want stolen, sold, lost or leaked.
- Adopt the most severe privacy on social media, otherwise you will all too easily stalked and social engineered.
- Do not use out of office for personal email as it confirms you a real address.
- Do not click links in email. Replicate links via search if you think it is genuine.
Mobiles
- Specialist phones are made that cannot be IMSI catchered to ID you by IMSI, intercept calls, deny service or track you (eg by police surveillance van), and software can protect normal phones, but any phone is vulnerable to ROM being overwritten such as by a Java card STK attack by network, SIM manufacturer or phone manufacturer or SIMjacking, so for ultimate security you would have to run your own network using trusted hardware. Even building your own network uses hardware that may have been compromised by governments.
- IMSI catchers could circumvent authentication and decryption if, for example, government orders the network to disable it or the IMSI catcher downgrades you to 2G by waiting for you to change tower so you send a tracking area update request, then the IMSI catcher sends a TAU reject message with EMM cause 7 to force your SIM off of LTE such as 4G into a lower generation network such as 3G. Hackers want you off of 4G as it has authentication, better encryption and does not mindlessly go with the strongest tower, but some cell site simulators run in 4G without having to kick you down to 2G, for example, by attacking pre-authentication messages in 4G or 5G during RRC connection which can include IMSI and even GPS coordinates. They can spoof a 4G mast by ID theft or frequency maximising. They can track you by finding out which cell you are in with a laptop running something like Ubuntu and some Github code and a software defined radio like a Hack RF One, looking for broadcasts of lists of IMSIs and IMEIs during radio resource control, or tricking your phone to leak GPS or listening in on phone’s broadcast of signal strengths for each tower to allow triangulation. An attacker can roughly locate your phone by texting it or ringing momentarily several times to identify the location area, then identify the cell tower by Whatsapping you, then narrowing down to a TMSI to target. They can then pinpoint you with an specialist IMSI catcher by sending you a RRC connection reconfiguration command to trick your phone to reply with signal strengths of the three nearest masts, sometimes extracting the locationinfo-r10 field containing your GPS coordinate. Alternatively the network can use your nearest mast to paint you into a polygon. Some IMSI catchers may pretend to be from another location area thus force your phone to reveal its IMSI. A specialist IMSI catcher could launch a denial of service with EMM cause 8 to force you off non LTE too so you are in airplane mode, while other attacks choose between denying calls, texts and data. Some IMSI catchers can clone your phone to send fake texts on your behalf. To detect IMSI catchers you need gear to spot temporary base stations with inexplicably little traffic or suddenly higher power. You could try apps like Darshark, AIMSICD, SnoopSnitch, GSM Spyfinder or Cell Spy Catcher, or radio based versions like Sitch, Seaglass or Overwatch, but some apps need rooted phone to work at their best and all only see what they connect to, and all suffer limited reliability, whereas radio based detectors are more reliable but need more hardware like a laptop Linux server, raspberry pi, three synchronised omidirectional antenna and a GPS dongle, which you use to scan towers, trilaterate them then compare to known cells and look for changing parameters (country code, network code, physical ID, sector ID and tracking area code), location and strength. You can look up cell site simulator detection projects like FADe and Crocodile Hunter (which can trace cell site simulators to within 150 feet). Transmitting using radio defined radio to get maximum clues from a cell might be illegal, however. To get high assurance you need historic data to see what has changed in the area. Beware IMSI catchers are available in backpacks which police walk along with in plain sight and products like GSSI’s Suricatch (jump to 8.30) can link them to video cameras hidden in dummy fuse boxes with giveaway smoked glass fronts on lampposts.

- Such tools can be bought on the black market for £20,000, while better versions sold only to governments cost more like £30,000, and are openly sold in Israel and Saudi Arabia, and with knowhow you can just build your own one – if you know C++, Python, APIs, Raspberry Pi, GPS, SDR and LTE etc. Other attacks include 5V 15W 40m radius backpack jammers (or 12V 250W versions for vans) which force all mobiles nearby to GSM, allowing listening in of one or all numbers, and direction finders to find a phone after forcing it to broadcast through hacking it with an IMSI catcher. See PKI for examples of earlier generation technology and assume governments can buy or build better. Common brands are Stingray and Hailstorm. Stingray has a smaller brother call Kingfish which law enforcement can carry on foot to narrow down searches. DRT’s dirtbox can for example track 10,000 IMSIs from a plane. Models include the DRT 1101B (voice interceptor for target list up to 10,000, c. £80K) and DRT4411B (backpack version, c. £40K). Other fixed wing geo products in the USA include Garuda Gbox (can locate up to 1,000 GSM phones from a drone, c. £185K) Carman (GSM hacker for up to 500 targets, with 5 mile range, c. £130K), Typhoon (c. £175K), SR Technologies Windjammer (Thuraya INMARSAT satellite simulator, c. £200K), Radiance geolocator, Vendor West Raven geolocator (c. £800K), Rincon Deerpark geolocator (£250K), BAE Traveler geolocator (c. £750K), Adder, Nebula and Icarus.


- Other products used in the USA on the ground include the QRC Autonomous (GSM wireless hacker, c. £35K), Blackfin (bodyworn GSM hacker, c. £75K), Sagem OTT 488 (c. £10K), Nemo Handy N95 (c. £10K) and QRC ICS2 (c. £200K, running Decode Pro). Products like Hawk Analytics’ CellHawk lets law enforcement who have obtained a ‘tower dump’ of all calls and locations to map connections and movements. Adversaries may be criminals, spies, government or private detectives.
- Other gadgets include the Genesis phone used by NSA, which is a spectrum analyser, recorder and direction finder built into a mobile costing about £15K, and phone direction finders costing around £70K like the Hollowpoint 4 SDR used by NSA.

- The least you should do to your mobile is use a trusted operating system, which you can get by buying a Google Pixel and flashing Graphene to it. If that is too complex you can install LineageOS to stop Google siphoning off data from an Android phone.
- Beware Apple and Android track location.
- Biometrics can be forced against you, so learn how to stop that.
- Disable GPS, location, wifi and bluetooth. That still leaves ultrasonic tracking.
- Browse via Tor, eg for Android using Orbot and Orfox. Sandbox your system whilst on Tor by using a virtual machine like Whonix or Linux Mint Cinnamon. Never log into accounts whilst on Tor. Do not customise Tor as that creates a browser fingerprint. Do not go full screen as that tells the site your screen size. Only enter text after copying it from a text editor, not straight into a website, which could analyse your typing style to ID you unless perhaps you have the patience to inject noise by sneaking in some mouse and arrow movement or can do without java functionality. Do not use your usual language style; consider apps like Quillbot. Do not browse what you usually browse.
- Use passphrases.
- Use encryption.
- Set your phone to factory reset on too many wrong passwords, and set up ‘find my device’ to remotely wipe a stolen phone while it is still on and connected.
- Do not ring the same group of people on multiple or subsequent devices or SIMs, as software like NSA Proton can tell it is the same caller.
- Consider a privacy hardened phone like Purism Librem.
- Buy a pack of lens covers for your devices.
- Avoid other people’s hotspots, use your mobile internet over VPN instead or at least avoid doing anything confidential on somebody else’s wifi – remembering just logging on will identify you.
- Buy a pack of microphone blocker like Mic-Lock, which is just a dummy earphone jack.
- Not all mobile hacks are cell site simulators. Exploits include LTE ghost telephonist, which in seconds allows a hacker to switch on your microphone and send SMS.
- Beware mobile passwords can be bypassed, for example, by a Graykey brute force box or Cellebrite.
- Locked iphones and some part of Tor can be cracked by L3Harris who sell exploits to Five Eyes.
Apps
- Zoom is designed to be hacked.
- Stay off of TikTok which is a surveillance tool.
- Stay off Facebook, which is a big data marketing tool.
- Stay off SMS, Messenger and Whatsapp (owned by NSA front hackers Facebook). Use privacy messenging such as Signal, Silence (if you must use SMS), or Wickrme or Briar (peer to peer via Tor) instead for encrypted anonymous messenging.
- Use OsmAnd in GPS & airplane mode for navigation.
- Use ObscuraCam or ImageScrubber to blur and remove metadata from photo uploads. Beware GCHQ can deblur. Metadata can also be stripped by sending via Signal or uploading a screenshot instead. Signal has a blur tool.
- Google is Five Eyes spyware, tracking everything via search and phone numbers, and tracks dissidents, so use DuckDuckGo, Startpage.com, Searx.me or Qwant.com instead. For the same reason avoid Google’s Gmail which tracks anonymous accounts and sells your emails.
- VPN is part of the journey to security, but takes a lot of work to contribute much on its own. It should be paid for to be reliable, eg Azire, Black, Boleh, Nord, Mulvad or Trust.zone, and outside five eyes countries to avoid your own government spying on you too easily, in fact ideally outside Fourteen Eyes countries as per the list on ThatOnePrivacySite such as Boleh or Nord, and look for vendors who use OpenVPN, block IPv6 leaks, allow PGP encryption, include a kill switch, take bitcoin, do not log you or traffic with persistent cookies, trackers or proprietary APIs or ask for personal details and are in a safer jurisdiction. You have no way of knowing whether you can trust a warrant canary. Beware VPNs can still be compromised by whoever takes control of the server.
- Sign up for secure mail such as ProtonMail, Tutanota, Mailfence or Disroot, don’t use your name or a recovery email address linked to your identity, and use different accounts for everything.
- Remove app permissions. Only give network access to trusted apps.
- Replace Play Store and Apple Store apps with F-Droid versions or go without.
- Replace social media apps, to avoid libraries, APIs and Google Services etc, with their Progressive Web Apps, eg NewPipe to access Youtube.
- Be aware all your free emails are read by the provider: you are the product.
- Replace your browser with Brave. Microsoft Edge sells your data.
- Consider using a password manager, such as Lastpass.
- Use passwords of strings of five words for general accounts, and six words for high risk targets like your device, encryption, email and password manager.
- Security question answers should be randomly generated – do not use your real pet’s name etc.
- Use two factor authentication, ideally with a dongle like Nitrokey, Yubikey, Google Titan, Cisco, Thetis or FEITAN running U2F, or running WebAuthn, or at least an app like Authy, DuoMobile, Lastpass, Microsoft or Google Authenticator, or andOTP for one time passwords, rather than SMS which can be spoofed, SIM-swapped, phished or subject to SS7 hack. Unfortunately many accounts will allow SMS resets regardless.
- Create social media accounts while IP masked, in a false name, with anonymous email address and no phone number. If an account demands a phone number then ideally avoid it, or at least use a separate burner SIM for each account, although privacy could be undermined by multiple SIMs being used at the same address. Do not upload photos of you or photos with metadata. Review security and privacy settings. If you must upload a photo of you then ensure it is unique for each site to prevent reverse image search. Untag yourself and asks friends not to tag you.
- Beware when choosing hosts that as well as Five Eyes, there is nine eyes adding Denmark, Netherlands, Norway and France, Fourteen Eyes (Sigint Seniors Europe, started in 1982, expanded after 2001, communicating over Sigdasys) adding Belgium, Germany, Italy, Spain and Seden, and twenty countries share metadata with GCHQ including South Korea and Japan (due to fears of North Korea), Sigint Seniors Pacific (started in 2005 with Five Eyes plus South Korea, Singapore, Thailand, with France and India coming in later, communicating over Crushed Ice for data up to Secret classification), they have a wider panel of third party countries who cooperate such as Israel, Algeria and Pakistan, and anyone in a coalition such as NATO, AFSC, SSEUR (Belgium, Denmark, France, Germany, Italy, Netherlands, Norway, Spain, Sweden) or SSPAC is assumed a partner too. NSA refer to focussed cooperation with tier B third parties which are basically South Korea and Europe.
On the street
- Learn how to counter facial recognition. Delete, disable and cover microphones and cameras on your person (eg camera covers), at home (use firewall camera protection such as comes with Bitdefender, and unplug when not needed) and mask up outside. Governments have a database called Clearview that can recognise stored faces with almost perfect accuracy, the only limit being how fast samples can be uploaded; luckily there is not yet a way to feed in all cctv live Personal of Interest-style. Beware the more shots you share, the easier someone can deepfake you. Wear sunglasses, mask, a bland hairstyle, hide tattoos and wear greyman clothes. You may have to even wear gloves and goggles against irritants.
- Follow EFF protest advice.
- Avoid wifi as that can be cloned by police.
- Avoid using a phone connected to your apps as police can ID you via those thanks to Google or Apple if they can’t link the phone to you directly.
- Phones can be hacked or cloned, eg using BlueBorne.
- Beware Google track activity on your Android phone via an advertising ID and track your location even if you opt out of location.
- Use a GSM burner phone with anonymous prepaid SIM activated away from home, then put in airplane mode, turn GPS off, power off and put in a Faraday bag and only reduce security in reverse order of that. Even better, remove the SIM and battery while within 50 miles of home. Don’t carry other devices with you. Don’t use your usual routes or SIM or call the usual people or call from the usual place. Don’t buy electronically while out as for example Google buy and deanonymise your purchases regardless of what vendors and banks do with your transactions. Even a carefully used burner phone can be cracked by surveilling the shop or voice recognition or matching links to you to the shop’s location such as your group buying cheap Nokias at once or sticking out as a rare closed loop.
- Switch on encrypt disk.
- Use passcode rather than biometrics.
- Try to avoid carrying devices.
- Store data on the cloud with client side encryption so you can wipe it from your device with a factory reset and dispose of any memory card if expecting trouble with no way for anyone to access the data even if they hack the device and force the host to cooperate. Some phones can upload to cloud then delete at the press of a button. Remember the deleted data could be forensically recovered from your device or ordered from your cloud host.
- Try to keep phone powered off. If you fear malware that fakes power off you would have to remove the battery.
- Consider a Chromebook to keep data off the machine and on the cloud.
- Coming through ports police may s7 your phone and pass to GCHQ for upload to LuckyStrike weak links database, but probably only as a frequent traveller from overseas.
- Browse in private mode.
- If about to be compromised send essential files to a friend on Signal before deleting.
- Avoid ANPR cameras whether by route or number plate, these will be on roads or nearby a protest, possibly looking like speed cameras or CCTV.
- Avoid buying tickets by card.
- If taking photos by smartphone use the camera without unlock function such as double pressing power on an Android Pixel.
- In case your phone is confiscated be ready to use another device to remote wipe it and revoke app access.
- Be aware that police may install gunshot detectors or other microphones.
- Be aware that networks can tell government everywhere a phone has been while connected or every phone in an area. Software like NSA Cotraveler plots who was near who.
- Be aware that wifi linked to you by your MAC could be detected hundreds of miles away unless wifi is switched off even if not connected. Investigate whether your phone accepts change of MAC.
- Look out for:
- body worn cameras in glasses, hats, helmets, pockets, buttons and on chest and shoulder (dome or bullet cam),
- biometric scanners,
- CCTV, perhaps on telescopic poles on vehicles or trailers,
- FLIR cameras, perhaps on poles, with distinctive purple or coloured shine to lens,
- drones, you may see operators holding controls or the drone may be tethered for extended duty,
- surveillance vans, may have aerials such as for mobile jamming,
- helicopters with searchlights, loudhailers or FLIR,
- streetlamps with SmartCity microphones or cameras.
Circumventing censorship
- It times of unrest, government may try to kick you off some or all of the internet.
- This takes the form of internet shutdown (usually land line and mobile, but often just mobile), by:
- manipulating border gateway protocol or DNS (poisoning or hijacking, or ordering deletion or misdirection),
- platform blocks (usually social media, especially facebook, instagram, twitter, whatsapp and telegram, but occasionally youtube, periscope, Google+, Foursquare, Drive and LinkedIn / Slideshare),
- throttling (much rarer),
- URL blocks via ISPs,
- URL keyword filtering,
- packet filtering for excess keywords, or
- downgrade to 2G (sometimes only allowing access to whitelisted sites).
- Oppressive firewalls are built by firms like Cisco, Hacking Team, Gamma, Bluecoat and Amesys.
- Some restrictions are regional, usually along ethnic lines, typically when a video of police brutality goes viral or provide cover of darkness for death squads.
- Governments blame hate speech or fake news, when of course the reason is really protests or military crackdowns.
- Other ploys include:
- banning minorities from owning SIMs,
- requiring phone registration,
- taxing mobile internet out of existence,
- licensing internet providers and cybersecurity,
- hacking, DDoSing and attacking dissidents online via shills (eg HMG hire PR firms to troll citizens or promote policy for covid etc) and surveilling them,
- forcing citizens to use government internet cafes,
- forcing firms to issue fake X509 certificates,
- timing out non-government VPNs after one minute,
- blocking news sites, or
- simply not allowing mobile internet to be installed in the country.
- Throttling can target IP, MAC and protocols (via quality of service attack), and can use deep packet inspection or NIC or port partitioning or diversion through chokepoints.
- In wartime, methods may escalate to:
- DNS or border gateway protocol attacks and satellite jamming, or
- even EMP, cutting undersea cables or blowing up or pulling the power to switches, exchange points and landing points, although these are messier and affect other countries.
- Even in ‘peacetime’, platforms are taken down on a daily basis by state actors such as North Korea, Iran, Russia and China.
- The average country restricts the internet once a year, but it is actually about 35 countries doing it some six times a year. Whilst India is the worst offender, and most others are tinpot dictatorships, the UK has done it once, which was when police illegally) ordered Virgin to cut TFL’s tube station wifi to help stop climate protestors coordinating terrorism. Chad have cut off social media for 472 days, India have cut off internet in regions for 175 days and Mynamar have cut off internet in regions for 71 days. A typical year see some twenty shutdowns lasting over a week.
- To try to resist censorship:
- use IP addresses instead of URLs,
- modify host files,
- use https to hide which page within a site you visit,
- change ISP and DNS resolver (eg to Cloudflare, Comcast or NextDNS),
- use encrypted DNS on Firefox (DNS over HTTPS) or Android (DNS over TLS) to hide which site you visit,
- run your own VPN server to get a random IP address (but will lose anonymity),
- use an anonymiser like Anonymizer,
- look for pages in google cache or Waybackmachine,
- try Google mobile search to view via html or screenshot,
- try screen resolution checkers like Duplichecker to view pages below the radar,
- use short URL such as Tinyurl,
- use privacy search engines that can hide where you search from,
- use VPN and configured Tor (although countries such as Venuezeula, China and Iran have blocked Tor, and Russian and Ethiopia have criminalised it), perhaps adding Psiphon private SSL proxy & SSH obfuscation layer to protect the VPN,
- VPNs might be able to bypass VPN blockers using multihop, running OpenVPN over TCP port 443, Obfsproxy stealth servers to defeat deep packet inspection, SOCKS proxy eg Shadowsocks, SSL tunnels or SSH tunnels eg Stunnel via a cooperative VPN provider such as AirVPN; for example, NordVPN can disguise clients as normal traffic,
- use peer to peer networks like Lantern, or Firechat off-grid Bluetooth / wifi messaging,
- hide text in images,
- share VPNs via the Xender app, USB and Bluetooth.
- To try to resist throttling:
Psyops
- You also need to stop your mind being hacked by psychological warfare.
JTRIG
- GCHQ are not the only player, but their Joint Threat Research Intelligence Group (‘JTRIG’) effects, known as online covert action, handle the cyber side of psyops, using a combination of information operations (influence or disruption) and technical disruption, to discredit, delay, deter, deny, disrupt, degrade and deceive, through fielding or recruiting spies, and forensics, hacking, open source data and persuasion using fake leaders to gain compliance. Operators are trained in spying (online HUMINT), strategic influence (info ops, eg through media) and disruption & computer network attack. This is covered in GCHQ’s The art of deception slideshow. Their psyops guide was written by ex-DSTL principal scientist Dr. Mandeep K. Dhami, who resigned from Cambridge and APA after she was outed as the author of what has been slammed as a dirty tricks manual.
- HUMINT involves using aliases and legends to conduct personality typing and establishing motives and mental illnesses, then appealing to emotions to persuade (herd) targets into new beliefs (such as that crime does not pay) on the basis that individuals believe crowds are wiser than oneself; in groups this involves taking over leadership by emphasising differences with the outside world and similarities within the group to buy credibility, before giving new commands to obey or doing the opposite to destroy it and recategorise members and outsiders, and reduce competitions between groups to reduce benefit of membership and create new identities, meanwhile conspiracy theories are battled or created, perhaps deploying apophenia to encourage members to see imaginary patterns and evil intention behind it; on social media it means creating disguised propaganda outlets.
- Influence involves using media to deceive, building relationships by looking familiar (mimicry) and making gradual self disclosure (social penetration), and turning made up stories into cultural beliefs (anchoring) with the help of subliminal softening up (priming), confirmation and hindsight bias, anchoring, priming, narrative and target audience analysis (TAA) (finding access and vulnerabilities, checking identity, location and carrying out PMESII analysis) to carry out scams.
- Disruption is supposed to be elegant, creative and intuitive, through carefully chosen channels, delivering a believable performance to tear an organisation apart from the inside, and potentially responding in real time.
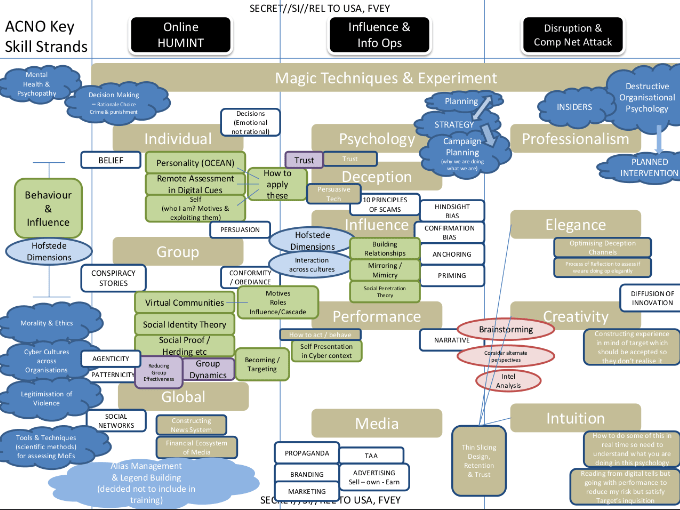
- They also gather limited intelligence, but that is mainly left to the rest of GCHQ signals. Covert investigators using unattributable internet access to provide colleagues with targets (people) and selectors (phone numbers etc). They are organised into ops, technical and JBOS.
- The ‘leaders’ are typically social media influencers co-opted or hired, or PR firms running bot farms.
- Techniques include conspiracy theories, hindsight bias, confirmation bias, anchoring, priming, propaganda (eg videos, accounts and spoofs), branding, advertising (eg to discourage terrorists and paedos) and marketing.
- Tactics include tapping Skype with Miniature Hero, stealing Facebook photos with Spring Bishop, false flag, fake victim, honeytraps (eg hosting extremists sites), hacking online polls with Underpass, deleting content, planting files on computers, leaking fake genuine secrets to networks, computers or spies, editing wikipedia, faking IP addresses, sending email (Badger) & sms (Warpath) blasts, deleting user accounts with Angry Pirate, inflating site views with Slipstream or traffic with Gateway, video takedowns (Silverlord, apparently by hacking the poster), 2P2 DDoS, targeted DoS with Predators Face, target’s ebay tracking with Elate, wikileaks tracking, forcing people to ring each other (Imperial Barge), fake posts and spoofing emails (Changeling) to friends, credential harvesting (recruiting journalists to spread stories). Spies and online monitoring is used to analyse targets to facilitate befriending online. There are often so many spies in forums that they accidentally spy on each other as they do not all share deconflict alias lists. Fake groups are created to take responsibility for attacks.
- Tricks deployed to deceive you include dissimulation (masking, repackaging and dazzling) and simulation (mimicking, inventing and decoying), repetition, faking a campaign end, distraction, attention grabbing and big lies covering small truths, cues, switching, beliefs, Haversack ruse, stress, Cialdini+2 influence (eg scarcity, flattery, favours, consistency, herding, social compliance, dishonesty, greed, deception and time), simulation and channeling.
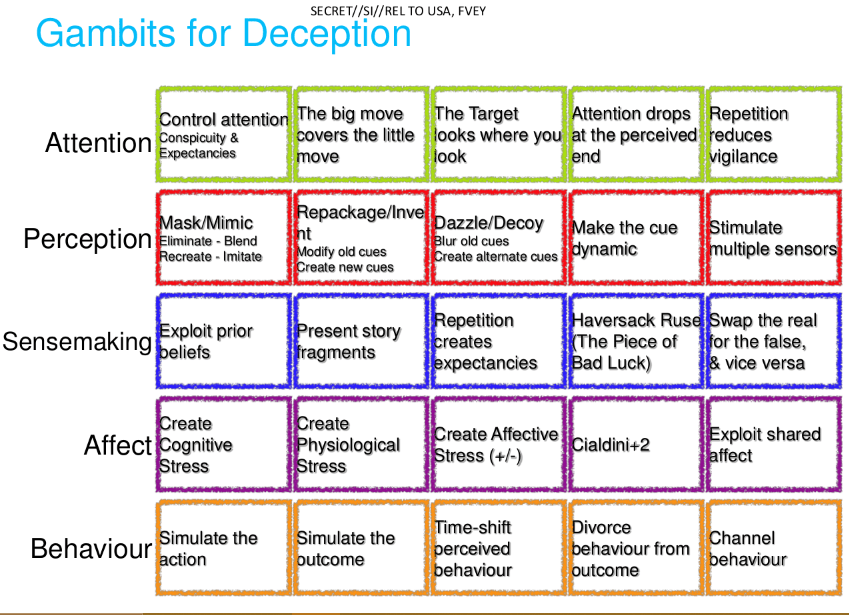
- Channels include text, chat, email, blogs, sites, social media and news media.
- If the task is to encourage non-compliance then tactics include questioning authority, giving examples of non-compliance and demonstrating adverse consequences of compliance.
- They try to destroy groups by injecting splits of personality or ideology, ie factions.
- They presumably do the same as NSA in discrediting targets eg by exposing porn, fraud or contradictory statements.
- This all means state actors like GCHQ engage in political warfare against citizens.
- Although, normally used against diplomats, they track hotel bookings and maybe car hire with Royal Concierge contact chaining government email addresses emailing luxury hotels, then hacking with close access technical operations and spying on guests with HUMINT.
- GCHQ also collect Prevent data from councils and brief government departments not only on national security but on collections relevant to policy, like health and climate change.
- JTRIG sometimes profile targets to customise attacks, however there is not much capacity to target random dissidents, you would have to be deemed a priority gangster (trafficker, fraudster, paedo, drug smuggler or hacktivist) or terrorist, spy or combatant first. The main risk to dissidents is being labelled a domestic extremist (JTRIG spied on EDL) and thus a cyber criminal, but potentially any crime suspect can be targeted to have their reputation destroyed by the serious crime effects team or be subjected to psyops through the human sciences operations cell, most of whose training is on scams. This could come about not just through MI5, SOCA or the Met, but merely by coming on the radar of National Public Order & Intelligence Unit.
- One JTRIG task is gaining access to sources that are about to be lost to encryption.
- Other psyop agencies include the 77th Brigade who supposedly concentrate on support to military operations in theatre, but are also accused of waging a psyop against lockdown and vax sceptics (their commander was on the daily Covid TV briefing panel), although some of that work was against Russia who were discrediting the Oxford vax after they stole and rebranded it as Sputnik. JTRIG SMO say they work with special forces and JIEDAC. In- theatre ruses include leaflets and TV and radio channels.

- The rule of engagements for psyops is that it has to be within mission and proportionate, and either has to be legal or authorised by the minister if breaching UK law or in line with Five Eyes policy if breaching international law.
RICU
- The Home Office’s Research Information & Communications Unit is an anti jihad psyop team staffed from Home Office, FCO and MHCLG. It has a Campaigns team for domestic and international, a Monitoring & Coordination team for analysing reactions, and an Insight & Analysis team for targeting audiences.
- Whilst is has been criticised for manipulating muslims and journalists in a bid to head off right wing retaliation, more disturbing is that it runs controlled spontaneity for terror attacks to ‘Dianarise’ the backlash so as to prevent the public realising they are in WWIII after a muslim invasion of enemy combatants and to distract voters from rioting. This involves government hashtags (#WeStandTogether), posters, vigils, flower distributors, news articles, PR agencies like Saatchi’s Horizon (a front for Zinc), social media and immans supplied by Faith Associates led by Shaukat Warraich that the public assume are genuine. The worst was perhaps the Sun dedicating an edition to a fake Union Jack hijab in 2014 to cover up that one in three UK muslims support terror.
Psyops explained
- Psyops are communications (products) disseminated to influence a target audience’s attitudes, perception and behaviour, subject to policy limitations, towards political and military objectives (themes). Objectives might be crisis response, conflict prevention or combat.
- Supposedly the UK prefers white attribution to preserve credibility but may have to go grey or black to hide the real propaganda source. Likewise the UK supposedly prefers true propaganda to preserve credibility; this does happen, eg leaking embarrassing truths about the enemy.
- Frontline operators will have reachback to HQ support.
- Counter propaganda involves shielding the target or attacking facts.
- Psyops can include persuading populations to support NATO or at least accept its intervention or stop supporting enemy forces, or enemy forces to give up or at least become demoralised or believe NATO is more powerful than it is. It can help civil agencies get cooperation and civil agencies can help psyops work.
- Psyops can involve teams for test and evaluation, media monitoring, tactical support and product development. They require intelligence sources and linguistics.
- Whilst planes might drop leaflets, sometimes the planes are the psyop.
- In peacetime pysops might be for alliance building, training, peacekeeping, humanitarian assistance, counter insurgency or shaping battlespace in major combat.
- A psyop may requires spies in the camp and external expertise.
Info ops
- Psyops’ cousin, info ops, is:
- information activities against the information environment of information and information systems,
- to affect will, understanding and capability,
- typically by:
- protecting NATO data and attitudes to NATO, whilst
- attacking attitudes to adversaries and attacking their data.
- Both psyops and info ops are species of SRATCOM (influencing attitudes and behaviour by communications).
- Operators may try to:
- canalise opinion,
- coerce behaviour,
- contain disinformation,
- deceive decision makers,
- damage morale, target value or decision making,
- deny the airwaves,
- detect hackers, and
- deter enemies,
- Info ops include:
- psyops,
- presence-posture-profile (eg wearing berets instead of helmets),
- OPSEC,
- INFOSEC,
- deception,
- electronic warfare (to silence the adversary),
- destruction of command & control,
- key leader engagement,
- CNO (hacking and cyber defence),
- civil military cooperation (for spying, advice and bribery through humanitarian assistance) and
- ‘special capabilities’ (Five Eyes surveillance).
- Info ops involve:
- analysts,
- engineers,
- advisers,
- trainers,
- planners,
- special forces and
- electronic warfare, security, deception, targeting, liaison and CNO officers.
- Info ops is one component of influence within joint action capabilities and activities, other joint actions being:
- manoeuvres (gaining advantage indirectly through time and space),
- fires (physical effects to blind and blow up the enemy) and
- outreach (stabilisation, eg security or infrastructure building),
- all targeting will, understanding and capability, eg ‘play ball with NATO and you get infrastructure’, ‘resist and you get blown up’.
- Other components of influence include media, OPSEC and civil military cooperation.
Counter-psyops
- Of a group member, ask yourself are they:
- asking for small favours,
- mimicking,
- overaccommodating,
- inexplicably unwilling to reveal themselves,
- suffering continuity issues between shifts,
- playing with emotions, especially ego up or down,
- suddenly displaying high metrics,
- being talkative, assertive, diverse and exaggerating,
- using turns of phrase, or even whole posts, you can find elsewhere,
- posting assertions without argument, or using stereotypes,
- trying to discredit, distract or split the group,
- trying to wangle their way to become a moderator,
- are users suddenly replying to old posts at about the same time to push an embarrassing post off the top?
- Of messaging:
- Are you sensing what you expect to rather than the truth?
- Is it customised to your personality?
- Is this person, message or site supporting government policy?
- Is it attacking your facts (eg claiming experimental vaccines are ‘safe and effective’)?
- Is it discouraging support for critics (eg dissenters are ‘damaging the NHS’ or ‘killing grandma’)?
- Is it demoralising critics (eg accusing them of being the ‘tin foil hat brigade’)?
- Is it making policy sound inevitable (eg ‘everyone will be vaccinated’)?
- Are replies delayed, irrelevant, hyperbolic, generalised and do they includes negatives?
- Of government:
- Is it hiring spies (eg forum infiltrators) or advisers (eg behavioural psychologists)?
- Is it bribing to get buyin or supporters (eg are thought leader critics mysteriously becoming supporters, or are supporters given favours like being allowed out of house arrest if they accept experimental drugs)?
- Is it lying or coercing (eg exaggerating or faking data, hiding alternative solutions, punishing dissenters with social restrictions)?
- Is it stopping leaks (eg bringing in MI5 to find dissenters in Downing Street)?
- Is it coopting the media (eg is MSM mysteriously and unanimously complicit)?
- Is it deploying the military (eg for ‘army for logistics’ or ‘GCHQ for data mining’)?
- Is it manoeuvring, destroying or nation building (eg abolishing the economy, abolishing the NHS, ‘Build Back Better’)?
- Of critics, are they being:
- demoralised (eg preventing earning a living, forming relationships or getting medical treatment, or telling you what to wear, what beauty treatments not to have, what hobbies not to have, where not to go, who not to see and what not to buy),
- confused (chopping and changing instructions, eg masks do not work then they do work, distancing does not work then it does work, lockdown works then it does not work so vax is needed, then vax does not work so lockdown is needed),
- deplatformed, or
- degraded in terms of strength (eg money, health and relationship taken away)?
- Look out for:
- Law of small numbers – drawing conclusions from small numbers of incidences
- Conditioning – eg crying wolf, disabling security same time every day is dismissed as benign error, or taking same route every time before suddenly veering off
- Controlling channels
- Increase noise to create ambiguity to increase uncertainty about rumbled truth
- Decrease noise to misdirect to increase certainty in the lie
- Alexrod’s assets husbanding – enemy may not reveal countermeasures until stakes are high, enemy may delay deception until it is too late to defend even though it looks like it will not happen
- Read Claire Wolfe’s ‘Rats’ Stop Snitching guide.
- Beware strangers suddenly asking you to misbehave.
- Beware strangers who are stereotypes of your group.
Cryptome has a Gentleman’s guide to forum spies.
Emergency coms
- Government will still be able to get their message out if they switch off public networks or their is damage or attack on some networks. They have a portfolio of resilient communications:
- ResilienceDirect web, for disaster responders to share plans, responses and lessons learned, classified up to Official Sensitive, provided by Airbox, accessed at Resilience.gov, with four components: collaborate (repositories), maps (including WhatThreeWords, learning (EPC Insight and JOL Online) and cyber hub.
- High Integrity Telephone System links police to government, originally over Government Resilience Extranet (replaced by ResilienceDirect, was sponsored by Civil Contingencies Secretariat (CSS) and DSTL Land Battlespace Systems, built by BT and Ultra Electronics Command and Control Systems using Atlas Collaborate browser application, replaced in 2013 due to clunkiness, lack of mapping and user lack of interest, options were replacing with G cloud and potentially joining forces with Rimnet or Nuclear Emergency Response Information Management System (‘Nerims’, also built by Ultra)) for classified content, works through Skynet5 if the PSTN collapses, provided by Paradigm Secure Communications via 1.2m diameter dishes using the single Airbus 4E satellite at 6 degrees east.
- Privilege access schemes:
- MTPAS (formerly ACCOLC) was launched by the CCS, whereby networks give responders (government and cat 1 & 2 responders and their partners), who are sponsored by Local Resilience Forums’ Telecommunications Sub Groups or government, a special SIM that stays connected when public access is throttled in the event that a Special Coordinating Group’s Police Gold Commander invokes it.
- Airwave sharers are allocated by Ofcom, and are normally emergency services and CCA responders. The UKIC have their own Airwave.
- In an emergency government could take over Floodline Warnings Direct‘s (replaced in 2018 by ‘gov.uk Notify‘ run by Fujitsu, typically sends 3 million emails and 2 millions texts per day, rated to Official Sensitive) Extended Direct Warnings which uses reverse 999 to play a message to 60,000 anonymised landlines per hour , Cell Broadcast System and social media to push alerts to land lines, mobiles and internet.
- The army in the form of 11th Signal Brigade and councils have used Raynet in emergencies for its volunteers’ VHF & UHF network.

I’m really enjoying the design and layout of your site. It’s a very easy on the eyes which makes it much more enjoyable for me to come here and visit more often. Did you hire out a designer to create your theme? Fantastic work!
LikeLike